Table of Contents Link to heading
- User Accounts and Groups
- Administrative Accounts
- Switching Users (su)
- Executing Privileged Commands
- User Accounts: /etc
- Passwords: /etc/shadow
- Types of Accounts
- Viewing User Information
- Viewing Current Users
- Viewing Login History
User Accounts and Groups Link to heading
User accounts designed to provide security since each person on the system must log in using a user account which either allows the person to access specific files and directories or disallows such access, accomplished using file permissions.
Each user belongs to at least one group (often many) to allow users to more easily share data that is stored in files with other users.
User and group account data is stored in database files. Knowing the content of these files allows you to better understand which users have access to files and directories on the system. These database files also contain vital security information that may affect the ability of a user to log in and access the system.
Several commands provide the ability to see user and group account information, as well as to switch from one user account to another (provided you have the appropriate authority to do so). These commands are valuable for investigating usage of the system, troubleshooting system problems, and monitoring unauthorised access to the system.
Administrative Accounts Link to heading
allows logging in to the system as the root user to execute a command that requires administrative or root privileges.
Risks with logging in as the root user:
- Everything about your session (background processes, executables) runs as the root user
- May forget you are logged in as root and run a command that could cause problems on the system
- May forget to log out to do their non-administrative work, allowing programs such as browsers and email clients to be run as the root user without restrictions on what they could do
Thus, it is not recommended to log in as the root user directly to perform
administrative tasks. If the root account is disabled, as it is on the Ubuntu
distribution, then administrative commands can be executed using the sudo
command. If the root account is enabled, then a regular user can execute the
su command to switch accounts to the root account.
Switching Users (su) Link to heading
The
sucommand allows a user to switch shell to another user.
- Using the login shell option results in fully configuring the new shell with settings of new user. If username is not specified su opens a new shell as root user.
- After pressing Enter, user must provide password of root user.
- Use the exit command to return to original shell (user account).
Commands:
Switch to superuser (requires the root password):
suSwitch to a given user (requires the user’s password):
su usernameSwitch to a given user and simulate a full login shell:
su - usernameExecute a command as another user:
su - username --command "command"
Executing Privileged Commands Link to heading
The
sudocommand allows a user to execute a single command as the superuser or another user.
- Can be used in distributions that do not allow root user login.
- Prompts for the user’s own password instead that of the root user.
- Results in an entry placed in a log file for accountability and reduces risk associated with using root.
Commands:
Run a command as the superuser:
sudo less /var/log/syslogEdit a file as the superuser with your default editor:
sudo --edit /etc/fstabRun a command as another user and/or group:
sudo --user=user --group=group id -aRepeat the last command prefixed with sudo (only in bash, zsh, etc.):
sudo !!Launch the default shell with superuser privileges and run login-specific files (.profile, .bash_profile, etc.):
sudo --loginLaunch the default shell with superuser privileges without changing the environment:
sudo --shellLaunch the default shell as the specified user, loading the user’s environment and reading login-specific files (.profile, .bash_profile, etc.):
sudo --login --user=usersudo --user=user --group=group id -aList the allowed (and forbidden) commands for the invoking user:
sudo --list
User Accounts: /etc Link to heading
contains files which contain account data of users and groups defined on the system.
The /etc/passwd file defines some account information for user accounts.
- Each line contains information about a single user.
- Name, password placeholder, user ID (UID), primary group ID, comment, home directory, and shell.
- Fields are separated by a colon
An efficient way to check if a specific user has been defined on a system is to
search the /etc/passwd file using the grep command. For example, to see
the account information for the user named sysadmin, use the following command:
grep sysadmin /etc/passwd
Passwords: /etc/shadow Link to heading
This file contains account information related to the user’s password.
However, only the root user is allowed to view the the file’s contents for security reasons.
| Field | Description |
|---|---|
| Username | Username of the account (matches username in /etc/passwd) |
| Password | Encrypted password for the account |
| Last Change | Last time password was changed |
| Min | Minimum number of days between password changes |
| Max | Max number of days password is valid |
| Warn | Number of days before password expiry in the system warns the user |
| Inactive | Grace period in which user’s password can be changed |
| Expire | Number of days when user accounts will expire (from January 1, 1970) |
| Reserved | Currently not used, this field is reserved for future use |
In addition to the grep command, another technique for retrieving user
information contained in the /etc/passwd and /etc/shadow files is to use
the getent command, which retrieves account information that is defined
locally, in files such as /etc/passwd and /etc/shadow, or on a network
directory server.
The general syntax of a getent command is:
getent database record
For example, the following command would retrieve account information for the sysadmin user from the /etc/passwd file:
getent passwd sysadmin
Commands:
Get list of all groups:
getent groupSee the members of a group:
getent group group_nameGet list of all services:
getent servicesFind a username by UID:
getent passwd 1000Perform a reverse DNS lookup:
getent hosts host

Types of Accounts Link to heading
User Account Link to heading
logs into the system using regular user accounts; UID 500 or > 1000 on some systems.
Root Account Link to heading
The root user has special access to the system and is provided to the account with a UID of 0.
System Account Link to heading
designed to provide accounts for services that are running on the system; 1 > UID > 499.
System accounts have some fields in the /etc/passwd and /etc/shadow that are different from other accounts:
- Rarely have home directories as they typically are not used to create or store files.
- Have a nologin program in the shell field
- Typically have an asterisk * character in place of the password field
Group Accounts Link to heading
Each user can be a member of one or more groups, which can also affect the level of access to the system.
Traditionally, UNIX systems limited users to belonging to no more than a total of 16 groups, but the recent Linux kernels support users with over 65,000 group memberships.
The /etc/passwd file defines the primary group membership for a user.
The /etc/group file is another colon-delimited file that defines supplemental (or secondary) group membership.
| Field | Description |
|---|---|
| Group Name | Field contains the group name. The system typically uses group IDs rather than group names. |
| Password Placeholder | While there are passwords for groups, they are rarely used in Linux. If the administrator makes a group password, it would be stored in the /etc/gshadow file. The x in this field is used to indicate that the password is not stored in this file. |
| GID | Unique group ID associated with a group. |
| User List | Lists members in the group. Users who are assigned to additional groups would have their username placed in this field. |
To view information about a specific group, either the grep or getent
commands can be used. For example, the following commands display the mail
group account information:
grep mail /etc/group
getent group mail
The groups command prints group memberships for a user.
Print group memberships for the current user:
groupsPrint group memberships for a list of users:
groups username1 username2 ...
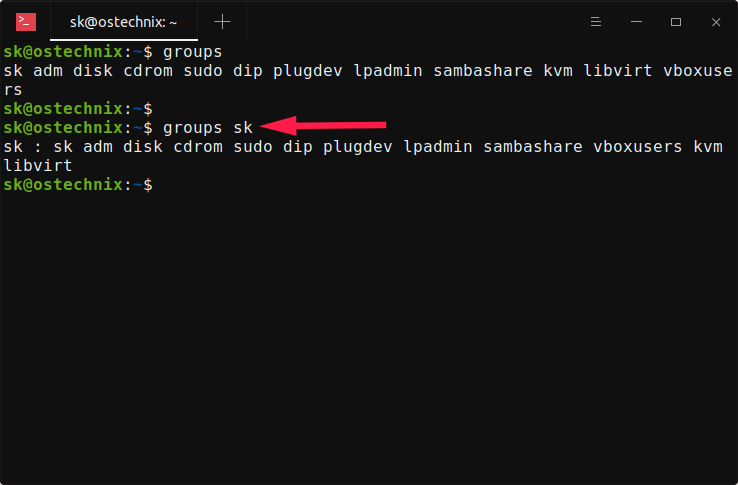
Other commands to work with groups include: groupadd, groupdel, and groupmod.
Viewing User Information Link to heading
id Command
Link to heading
displays current user and group identity.
Command:
Display current UID, GID, and groups to which they belong:
idDisplay the current UID as a number:
id -uDisplay the current GID as a number:
id -gDisplay all the GIDs:
id -GDisplay all the GIDs that have been resolved to group names:
id -GnDisplay an arbitrary UID, GID, and groups to which they belong:
id username

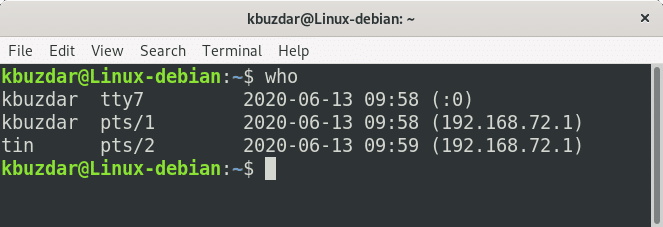
who command
Link to heading
displays who is logged in and related data (processes, boot time).
Output:
- Username - indicates user who is logged in and has an open session.
- Terminal - indicates which terminal window the user is working in.
- tty indicates a local login whereas pts indicates a pseudo terminal.
- Date - indicates when user logged in.
- A hostname means user logged in remotely.
- A colon and number means a graphical local login.
- No location info means user logged in via local command line.
Command:
Display the username, line, and time of all currently logged-in sessions:
whoDisplay information only for the current terminal session:
who am iDisplay all available information:
who -aDisplay all available information with table headers:
who -a -H
Viewing Current Users Link to heading
The
wcommand shows who is logged on and what they are doing; prints user login, TTY, remote host, login time, idle time, and current process.
Show logged-in users info:
wShow logged-in users info without a header:
w -h
The
userscommand displays a list of logged in users.
Print logged in usernames:
usersPrint logged in usernames according to a given file:
users /var/log/wmtp
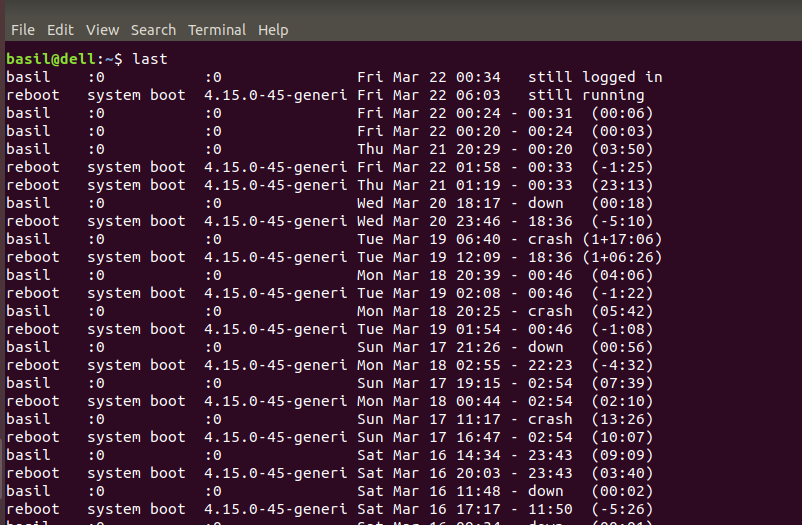
Viewing Login History Link to heading
The
lastcommand shows previous login sessions as well as current login information by examining the /var/log/wtmp file for all login records.
View last logins, their duration and other information as read from /var/log/wtmp:
lastSpecify how many of the last logins to show:
last -n login_countPrint the full date and time for entries and then display the hostname column last to prevent truncation:
last -F -aView all logins by a specific user and show the IP address instead of the hostname:
last username -iView all recorded reboots (i.e. the last logins of the pseudo user “reboot”):
last rebootView all recorded shutdowns (i.e. the last logins of the pseudo user “shutdown”):
last shutdown
