Table of Contents Link to heading
- Introduction
- Cryptography
- Symmetric (Secret-Key) Cryptography
- Asymmetric (Public-Key) Cryptography
- Cryptographic Hash Functions
- Digital Signatures
- Public Key Infrastructure (PKI)
Introduction Link to heading
Cryptography sits in between confidentiality and integrity, according to the CIA triad.
Problem Link to heading
I need to get a message to another person across the network, but it needs to be confidential.
Solution Link to heading
The message can be encrypted using an encryption algorithm and a key, then sent to the other person.
Cryptography Link to heading
If a message is to be encrypted by the sender, the receiver will need the parameters and the key used to encrypt so they can decrypt.
There are two main types of encryption algorithms:
- Symmetric algorithms: two parties have an encryption and decryption method for which they share a secret key.
- Asymmetric (or public key) algorithms: a user possesses a secret key as in symmetric cryptography but also a public key.
Let’s look at an example of cryptography. Can you answer this question?
IqersAwzl9tok8cFqlBMrgwsD9eEI/4qIt3UKa1GCM2CdDg2LPs2bpxPgidLYzpqRoRBCkRccVL+LOSY6tDTGg==
A - Yes
B - No
C - Too soon to tell
If you don’t understand the question, it is because it is encrypted. Visit the following website and use the supplied parameters to decrypt the encrypted question.
Paste in the question and then select the below parameters.
Parameters: Input Text Format: Base64 Algorithm used: AES Mode Used: Electronic Code Book (ECB) Key size: 128 bit Secret Key: 1122334455667788
Then choose Decrypt, then Decrypt to plain text.
Symmetric (Secret-Key) Cryptography Link to heading
a process that uses a single shared secret key for both the encryption of plaintext and the decryption of ciphertext.
An early symmetric cipher was the Caesar Cipher. This simple cipher used the alphabet and an agreed shift in position (between the sender and receiver). The original clear text message, one character at a time, is placed into the chart and shifted to the agreed position. This agreed shift is considered the “key” while the process of doing the shifting would be considered the “algorithm”.
If both parties know the key, the encrypted message can be decrypted by the receiver.
For example, if the key is 3, the message is shifted 3 positions to the right.
Plaintext: SECRET (the message)
Ciphertext: VHFUHW (the resulting encrypted message)
The below is a Substitution Cipher, each letter in the alphabet is randomly substituted with another and only the two parties sharing the file should know the method of substitution.
Plaintext: THE QUESTION
Ciphertext: RTQ ZYQORFAG
Two of the original symmetric algorithms were:
- DES (Data Encryption Standard): published by NIST in 1977
- 56 bit key length, this short key length can be broken relatively easy nowadays
- 3DES
- Encrypt DES 3 times in a row, much more robust but inefficient.
The most commonly used symmetric algorithms are AES-128, AES-192, and AES-256. (AES stands for Advanced Encryption Standard).
- NIST replacement for DES published in 2001
- 128 to 256 bit key length
Asymmetric (Public-Key) Cryptography Link to heading
a process that uses a pair of related keys: one public key (which may be known to others) and one private key (which may not be known by anyone other than the owner).
When someone wants to send an encrypted message, they can request the intended recipient’s public key and use it to encrypt the message before sending it. The recipient of the message can then decrypt the message using their related private key.
- One key is used to encrypt the message (public) and the other key is used to decrypt the message (private).
- Public versus private keys:
- Ciphertext encrypted with public key can be decrypted with private key
- Ciphertext encrypted with private key can be decrypted with public key.
- No need to establish a shared secret key.
- It is mathematically complex and can be slow to encrypt and decrypt => Symmetric Cryptography is much faster.
Let’s look at a use case scenario. We will break down the steps used in Asymmetric Cryptography. It allows us to establish secure communications even though there has been no opportunity to agree on a shared secret key ahead of time and the message is to be sent over an insecure connection like the Internet.
A wants to send a message to B over the Internet.
- Alice and Bob, each person, generates their own Public and Private key pair.
- Alice and Bob then exchange their Public keys to begin the communication process.
- Alice generates an AES key value using their Private key (e.g. 123456789abcdefg)
- Alice encrypts their message using the AES key which contains the rules and process used to encrypt.
- Alice encrypts her AES key using Bob’s Public key.
- Alice sends the encrypted message and the encrypted AES key to Bob.
- Bob can now decrypt Alice’s AES key using his Private key. Once Bob decrypts the AES key, he use it to decrypt the message using Alice’s Public key. Having Alice’s Public AES key proves the message came from Alice and can be trusted.
Cryptographic Hash Functions Link to heading
Problem Link to heading
I want to send a secure message to a destination and guarantee it has not been tampered with in transit. I want to have data integrity.
Solution Link to heading
A cryptographic hash function is a mathematical algorithm that takes data of variable size (the message) and maps it to a bit array of a fixed size, this output is known as the hash value or message digest.
The algorithm is one way, this means that a hash is always produced from cleartext but cannot be reversed.
Common Usage Link to heading
- Message integrity
- Digital signatures
- Password storage
Hashing Facts Link to heading
- No key needed
- One-way (plaintext to ciphertext)
- Not feasible to modify a message without changing its hash value
- Strong collision resistance—highly unlikely that any two inputs will hash to the same output
- Compression—usually a fixed size output, smaller than the input
Running the same plain text string (same input) through a hashing algorithm will always yield the same hash value (same output).

Potential Weakness of Hashing Link to heading
An adversary can generate a ‘dictionary’ text file - called rainbow tables - which relates passwords to the hash value (depending on the hashing algorithm used).
Dictionaries can be loaded into cracking software, such as John The Ripper, and a message digest run through the list. If a match is found the plaintext result is returned to the attacker.
There are online cracking tools available which are a concern to Security Administrators. Keeping any configuration files that may contain any hashes confidential is critical.
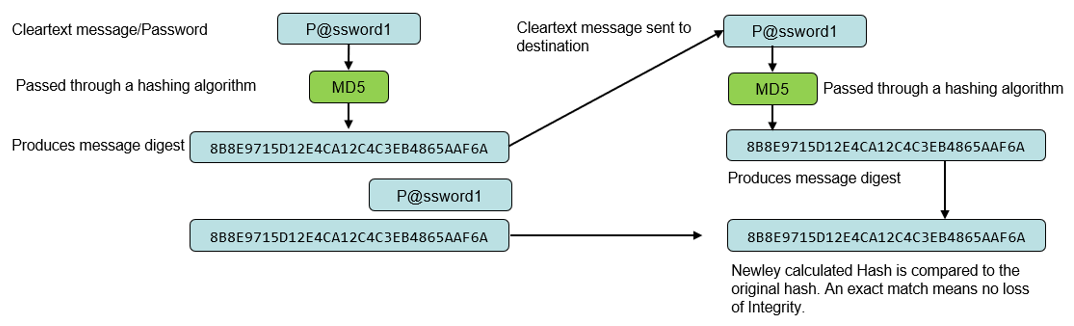
For example, the below encrypted text is an MD5 Hash value created on a Cisco Router:
- 2ac9cb7dc02b3c0083eb70898e549b63
- Browse to Crack Station website and paste the hash above into the field.
- Select Crack Hashes.
- The plaintext result is ‘Password1’.
Password Storage Link to heading
- Plaintext password is hashed and the result is stored in the database.
- Even if the hacker steals the database, they also have to crack the hashed passwords to figure out the original ones.
- During authentication, a user provides the plaintext password, which is hashed and compared to the stored hash values.
Example below extracted from one of my project.
| Username | Password |
|---|---|
| henry | 6cdc5a72dc333ad6d4eb71d4a84c8824726e7aac604a16b0257784083b7e188a |
| john | cc00499c113ff188075fb469da0607811653b67a47c6f627858f3811e7fc7910 |
| doe | d887800ff769b4f2467cd9aab1a8b514fb6c0c7933df826a11e6eda9595ab91b |
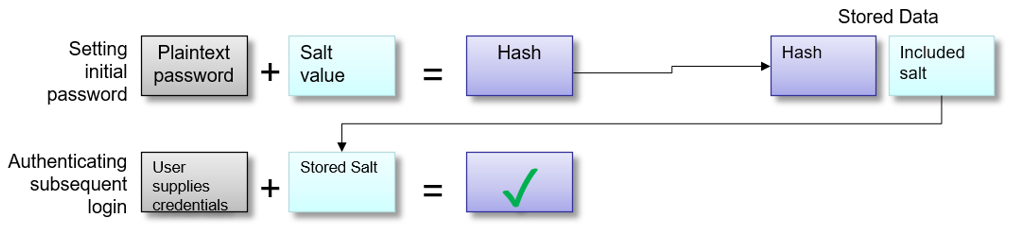
Salting a Hash Link to heading
To mitigate the damage that a hash table or a dictionary attack could cause, we ‘salt’ the passwords.
A salt makes a hash function look non-deterministic, which is good as we do not want to reveal duplicate passwords through our hashing.
Let’s say that we have password of “password1” and the salt “xyz”. We can salt that password by either appending or prepending the salt to it. This will yield either “password1xyz” or “xyzpassword1”.
The diagram below illustrates the process for salting a hash:
Digital Signatures Link to heading
refers to how we can use signatures to prove a file came from whom we expected it to come from.
- Asymmetric encryption and hashing can be used to implement digital signatures.
- Provides integrity assurance and non-repudiation.
- Commonly achieved by hashing the message, encrypting the hash using the sender’s private key and ‘attaching’ the encrypted hash to the message.
- The sender’s public key will also be sent with the message.
Let’s take an example where Alice is about to send a message to Bob.
- Alice applies an MD5 Hashing Algorithm to the plaintext message to create a message digest (Hash) 🔗.
- Alice uses her Private key to encrypt the message digest. As Alice is the only holder of this Private key, it proves the message comes from her (trust).
- Alice now sends the message, the encrypted message digest and her public key to Bob.
- Bob decrypts the message digest using Alice’s public key.
- Bob finally applies the same MD5 Hashing Algorithm to the message. If the resulting message digest (Hash) matches what was sent by Alice, then he knows the original message has not been tampered with and has maintained Integrity.
Public Key Infrastructure (PKI) Link to heading
binds public keys to entities, enables other entities to verify public key bindings, and provides the services needed for ongoing management of keys in a distributed system.
This system is most widely used in enabling trust in a HTTPS environment.
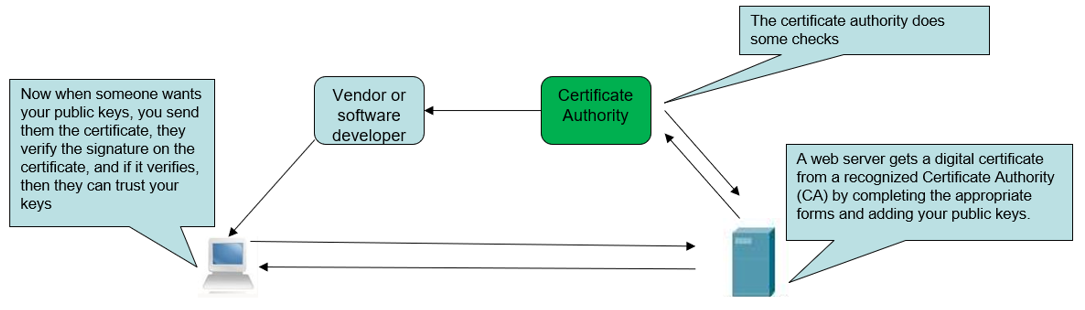
To illustrate, let’s look at a typical web browser and web server connection using SSL (HTTPS).
- Browser connects to server using SSL (HTTPS).
- Server responds with Server Certificate containing the public key of the web server.
- Browser verifies the certificate by checking the signature of the Certificate Authority (CA). To do this the CA certificate needs to be in the browser’s trusted store.
- Browser uses the public key from the certificate to agree a session key with the server.
- Web Browser and server encrypt data over the connection using the session key.
Vendors (e.g., operating system and software providers) trust the CA and include the public key of the CA in their products.