Table of Contents Link to heading
- The CIA Triad
- Confidentiality
- Integrity
- Availability
- How a Hacker sees a network
- How an Admin Sees a Network
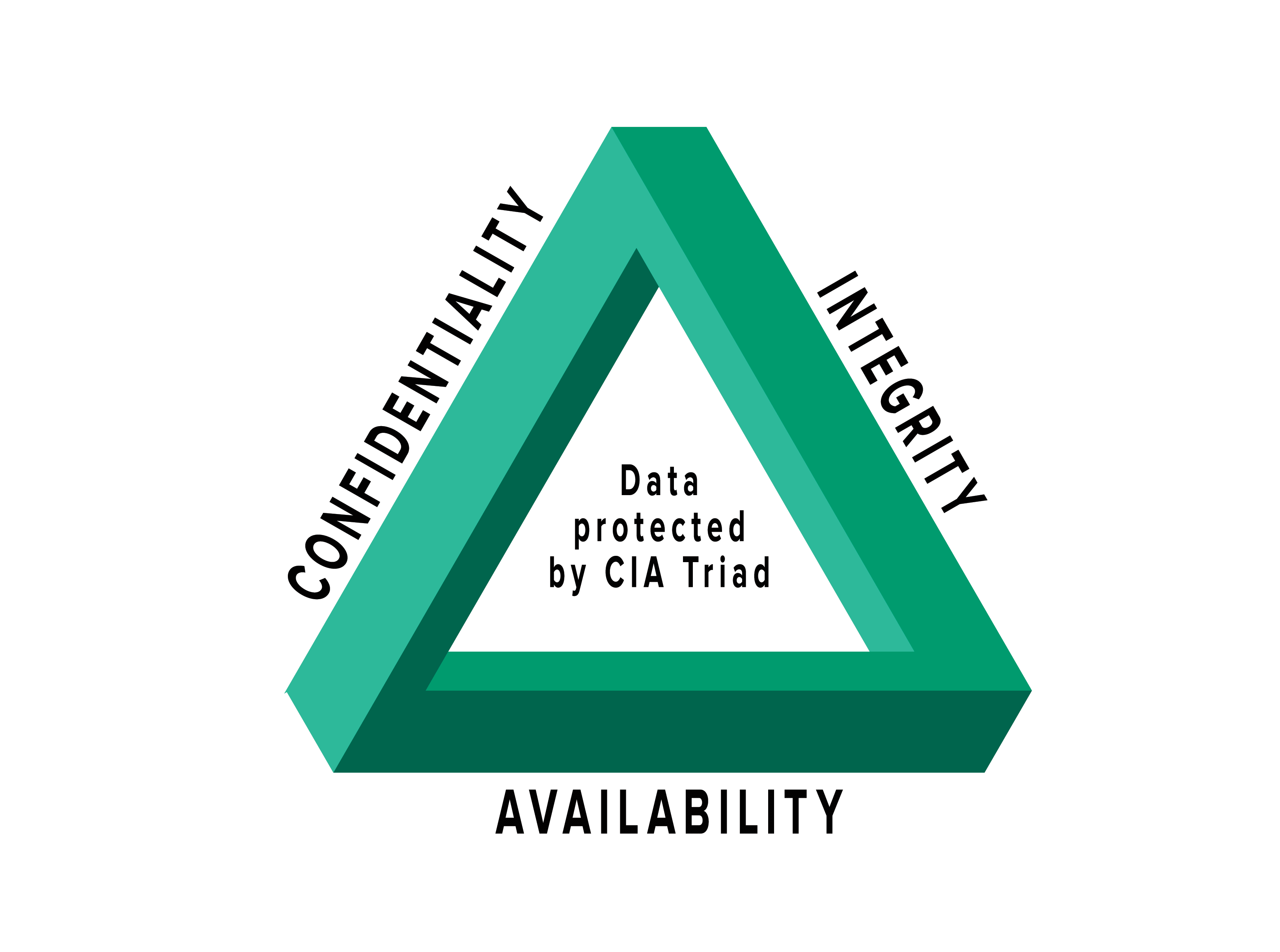
The CIA Triad Link to heading
a security model of confidentiality, integrity and availability is designed to guide policies for information security within an organisation.
Goal Link to heading
When we want to protect a network and the data contained within it.
Confidentiality Link to heading
the ability of a system to ensure that the information asset is viewed only by authorised entities.
Questions to ask could be:
- How secure is the information?
- How secure does the information need to be?
Providing this assurance can be described using three major steps:
Step 1 - Access Control Link to heading
Information must have controls that are capable of preventing some users from accessing the information.
These controls must be sufficiently granular depending on the rationale for the access control. The requirement for granularity is based partially on technical requirements and partially on benefits to the business.
How Link to heading
- Encryption of data both at rest and in transit
- Access control lists on network devices
- Non-technical – Physical security (locked doors, guards, fences)
- Role-based access control (RBAC)
Risks Link to heading
- Privilege Escalation
- Employee Negligence
- Bring your own device (BYOD)
- Man in the Middle Attacks (MITD Attack) 🔗
Step 2 - Authorisation Link to heading
access privileges granted to a user, program, or process or the act of granting those privileges.
It must be possible to limit access to information to authorised users.
Step 3 - Authentication Link to heading
the process of verifying the identity or other attributes claimed by or assumed of an entity (user, process, or device), or to verify the source and integrity of data.
An authentication system must be in place to validate the identity of those requesting access to data.
Authentication generally prefaces authorisation decisions (i.e. the system must identify the user before it can determine which authorisations the user holds).
How Link to heading
- Biometrics (fingerprint, iris patterns, or facial features)
- 2FA / MFA - the best way to secure any network, yet it is difficult (time-consuming) to implement.
- Something you know (username/password)
- Something you have (smart card)
- Something you are (fingerprint)
Risks Link to heading
- Social Engineering
- Phishing
- Shoulder Surfing
- Theft
Integrity Link to heading
the ability of a system to ensure that the information asset is modified only by authorised entities.
A more comprehensive definition is:
guarding against improper information modification or destruction, and includes ensuring information non-repudiation and authenticity.
Data is commonly made available for viewing by users, however they should not have the ability to change the data. Your course grades on the student portal is an example.
Questions to ask could be:
- How correct is the information sent and/or received?
- Has the data been modified during retrieval, in transit, or in storage (at rest)?
- If data has been modified without permission, do you have non-repudiation?
Assurance the sender of data is provided with proof of delivery and the recipient is provided with proof of the sender’s identity, so neither can later deny having processed the information.
How Link to heading
- Hashing of files and the information to ensure that it is accurate
- Provide checksums during the transmission of the data over the network
Example – Hacker imitates a lecturer to request a grade change for a student.
Hashing Link to heading
the process of transforming any given key or a string of characters into another value based on a specified hash function.
MD5 Link to heading
a widely used hash function that encodes a string of information into a 128-bit hash value (fingerprint).
MD5 is often used as a checksum to verify data integrity. However, due to its age, MD5 is also known to suffer from extensive hash collision vulnerabilities, but it is still one of the most widely used algorithms in the world.
For example, Cisco routers clear text password: enable password cisco123
The same password hashed using the MD5 hash: enable secret 5 $1$mERr$5.a6P4JqbNiMKOlusIfka/
Secure Hash Algorithm 2 (SHA-2) Link to heading
a set of six cryptographic hash functions with digests (hash values) that are 224, 256, 384 or 512 bits; developed by the National Security Agency (NSA).
Is it secure? Here is the hash value for [Password123]: 008c70392e3abfbd0fa47bbc2ed96aa99bd49e159727fcba0f2e6abeb3a9d601
Copy the hash above and paste it into this website.
Cyclic Redundancy Check (CRC) Link to heading
an error-detecting code often used for detection of accidental changes to data.
CRC is a number mathematically calculated, at the OSI data link layer, for a packet by its source computer and then recalculated by the destination computer. If the original and recalculated versions at the destination computer differ, the packet is corrupt and needs to be resent or ignored.
The most commonly used polynomial lengths are 9 bits (CRC-8), 17 bits (CRC-16), 33 bits (CRC-32), and 65 bits (CRC-64).
A CRC is called an n-bit CRC when its check value is n-bits. For a given n, multiple CRCs are possible, each with a different polynomial. Such a polynomial has highest degree n, and hence n + 1 terms (the polynomial has a length of n + 1). The remainder has length n. The CRC has a name of the form CRC-n-XXX.
Availability Link to heading
the ability of a system to ensure that the information asset is always accessible and usable upon the demand of authorised entities.
Questions to ask could be:
- How much up time is the system providing?
- Is the data always accessible to the end user?
There is limited utility in having a confidential and integral system if it is not available to authorised users.
This is the reason that “pulling the plug” during a cyberattack is rarely an option.
Denial-of-service (DoS) attacks, and its variants, are one of the most common attacks that affect availability.
How Link to heading
- Increase the redundancy of the system design by providing redundant components and data path
- Provide detailed backup strategies
- Establish a good disaster recovery plan
Risks Link to heading
- Hardware Failure
- Denial-of-service (DoS) attacks
- Distributed denial-of-service (DDoS) attacks
How a Hacker sees a network Link to heading
Confidentiality Link to heading
- Packet Capturing - These tools allow the attacker to view the data passing across a network.
- Keylogging - Installing a key logger will allow an attacker to attempt to capture login credentials.
- Access files - Once within a target system the attacker will attempt to locate sensitive files.
- Exfiltrate Data - Once data has been identified the attacker could choose to exfiltrate for off-site inspection.
- Delete data - If the attackers intent is disruption then they may choose to delete discovered files.
Integrity Link to heading
- Encrypt data - If the intent is ransomware, an attacker may encrypt data and demand a ransom for the decryption keys.
- MITD attacks - An ARP poisoning is the act of an attacker placing themselves between two hosts and capture the data flow.
- Delete data - A form of DOS attacks can be the attacker deleting or threatening to delete data.
Availability Link to heading
- Disrupt services (DoS, DDoS) - Any attack that prevents legitimate users of a resource from accessing that resource. Can be performed by bandwidth saturation (flooding) or service disruption.
- Deny access (Account manipulation) - Stealing or changing a users login details to prevent access.
How an Admin Sees a Network Link to heading
Confidentiality Link to heading
- Protect data - From the perspective of the CIA Triad this would involve encrypting data both at rest and in transit. If an attacker were to gain access the encryption would render the data unreadable unless they had the relevant decryption keys.
- Restrict access - A big part of providing confidentiality of data is controlling who has access to it. Providing access to only those who are authorised to use it and need to use it. This can be achieved through strong share permissions and multifactor authentication.
Integrity Link to heading
- Backup data - A backup is the process of making a copy of your systems data and storing it on a separate device, drive or physical location. A backup will protect your data from attacks on the integrity of your information. If an attack on integrity was to be performed and the data was encrypted a simple restore will mitigate the impact.
- Restore plan - Data restoration is the process of retrieving the encrypted, lost or corrupted data from your storage, media or files. A restore plan must be in place and tested to ensure it restores correctly and in a timely manner.
- Update - System or software update are critical in patching potential security holes in Operating Systems and applications. Left unpatched an application or OS could leave an open door into your network via exploits or vulnerabilities.
Availability Link to heading
- Firewalls - Watch this video for a simple explanation on what a firewall does.
- Intrusion Detection Systems (IDS) - Watch this video on how an IDS work, both Host based and Network Based.
- DDoS Protection Services - DDoS mitigation refers to the technique of protecting a targeted service or network from a distributed denial-of-service (DDoS) attack. By deploying specially designed network equipment or a cloud-based protection service, a targeted victim is able to mitigate the threat.
- Penetration (Pen) Test - This form of auditing a network is designed to identify any “holes” in your network’s perimeter. A specially trained ethical hacker will run a series of test to see if there are any vulnerabilities on the network and report back the results.