Table of Contents Link to heading
- Virtual Local Area Network (VLAN)
- Types of VLANs
- VLAN Trunk
- VLAN Trunking Protocol (VTP)
- Before and After VLAN Implementation
- VLAN Limits
- 802.1Q Tagging Method
- Cisco IOS Commands
- Dynamic Trunking Protocol (DTP)
- VLAN Design Best Practices
Virtual Local Area Network (VLAN) Link to heading
- A port (interface) on a switch, or simply a switch port, with only a singular
VLAN configured on it is called an access port.
- Access ports are most often used to connect host devices, such as computers and printers. By default on Cisco switches, all switch ports are access ports.
- With VLAN, remember that just because two computers are physically connected to the same switch does not mean that they can communicate. VLANs contain/isolate broadcast traffic, where you need a router to move traffic between VLANs.
- If multiple VLANs are configured, each must be associated with a unique subnet or network ID.
- VLANs helps to:
- Make it easy for network administrators to partition a single switched network to match the functional and security requirements of their systems without having to run new cables or make major changes in their current network infrastructure.
- Isolate broadcasts, multicasts, and unicasts in the individual VLAN.
- Set up by larger businesses to re-partition devices for better traffic management.
- Improve the overall performance of a network by grouping together devices that communicate most frequently or separating different types of traffic.
- Make implementing security policies easier by allowing a higher degree of control over which devices have access to each other.
- Provide additional security since traffic must traverse a L3 device to move between VLAN, where access control list can be implemented to filter traffic.
- Save computing resources and bandwidth with smaller broadcast domains.
| Benefit | Description |
|---|---|
| Simpler management | Similar groups will need similar applications and other network resources |
| Improved security | Only users in the same VLAN can communicate together |
| Improved IT efficiency | VLANs can group devices with similar requirements, e.g. faculty vs. students |
| Reduced Cost | One switch can support multiple groups or VLANs |
| Better performance | Small broadcast domains reduce traffic, improving bandwidth |
| Smaller broadcast domains | Dividing the LAN reduces the number of broadcast domains |
Types of VLANs Link to heading
- Data (or user) VLAN
- Configured to carry only date (user-generated) traffic.
- Not used for carrying management or voice traffic.
- Divides the whole network into 2 groups: one group of users and one group of devices.
- Default VLAN
- All switch ports are members of the default VLAN (and therefore parts of the same broadcast domain) when the switch is reset to factory defaults.
- It is the default for management, data, and native VLANs.
- VLAN 1 is the default VLAN for Cisco switches and cannot be renamed or deleted.
- Black Hole (or dead-end) VLAN
- Comprises all unused switch ports - not used for anything on the network
- so that any unauthorised device connecting to an unused switch port will be prevented from communicating beyond the switch to which it is connected.
- Does not have DHCP, Inter-VLAN routing, or device management enabled. This keeps the other VLANs more secure.
- Comprises all unused switch ports - not used for anything on the network
- Native VLAN
- Serves as a common identifier on opposing ends of a IEEE 802.1Q trunk link.
- Supports traffic coming from many VLANs (tagged traffic) as well as traffic that does not come from a VLAN (untagged traffic).
- Only one native VLAN can be assigned to a trunk port.
- All untagged traffic received on this port will become a member of the native VLAN.
- Frames belonging to the native VLAN are not tagged when being sent out a trunk port.
- Native VLANs pose a security risk, allowing an attacker to hop to another
VLAN by double-tagging a frame.
- Read more at 🔗.
- Management VLAN
- Used to remotely manage, control, and monitor the devices in your network using Telnet, SSH, SNMP, syslog, or Cisco’s FindIT.
- Should never be carried with user data traffic.
- To communicate remotely with a Cisco switch for management purposes, the switch must have an IP address configured on the management VLAN.
- When all management traffic is on a separate VLAN, it is much harder for unauthorised users to make changes to your network or monitor network traffic.
- The VLAN number is the SVI number on the L2 Switch.
- Voice VLAN
- Configured to carry IP voice (Voice over IP - VoIP) traffic from an IP phone.
- Must be separated from other traffic since voice traffic needs:
- Guaranteed bandwidth,
- High Quality of Service (QoS) priority,
- Less than 150ms delay from sender to receiver,
- Ability to avoid congestion.
- Modern networks must be built around supporting low-latency, high priority voice traffic.
VLAN Trunk Link to heading
- A VLAN trunk does not belong to a specific VLAN; rather, it serves as a conduit for VLANs between switches.
- Trunks are able to:
- Carry more than one VLAN,
- Extend the VLANs across an entire network,
- Support all VLANs by default,
- Tag frames using the IEEE 802.1Q protocol (dot1q).
- An example of trunking usage is a DHCP server, since it might need to assign IP addresses to users across multiple VLANs.
The example below shows a small switched network with a trunk link between S1 and S2 carrying multiple VLAN traffic.
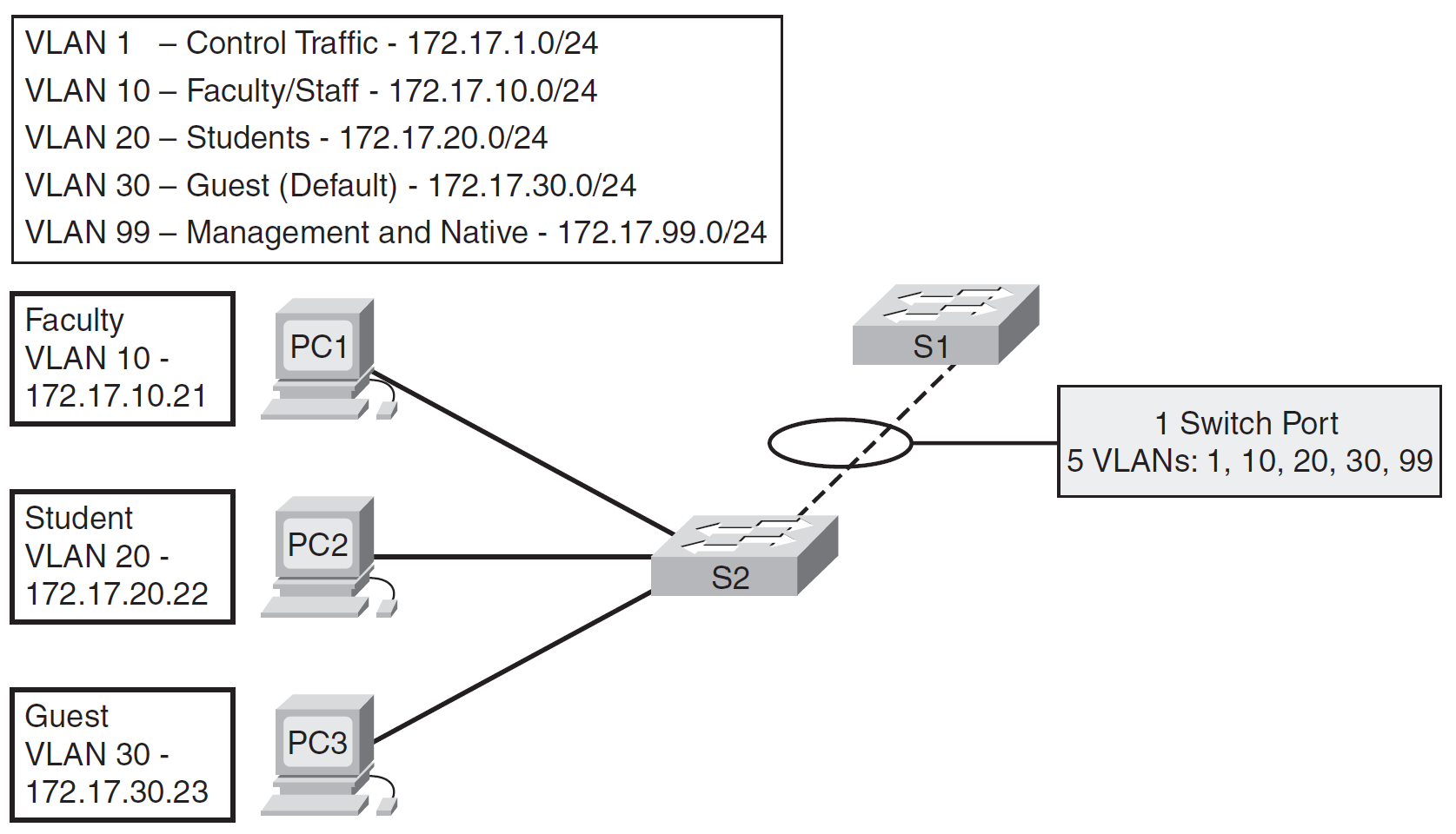
VLAN Trunking Protocol (VTP) Link to heading
- VTP requires that all participating switches join a VTP domain. Switches must belong to the same domain to share VLAN information, and a switch can only belong to a single domain.
- A VTP domain (or a VLAN management domain) consists of trunked switches that are under the same administrative control (sharing the same VTP domain name).
- VTP server mode requires a domain name. If the switch has a trunk connection to a VTP domain, the switch learns the domain name from the VTP server in the domain.
- VTP helps to:
- Minimise misconfigurations and configuration inconsistencies that can result in a number of problems, such as duplicate VLAN names, incorrect VLAN-type specifications, and security violations.
- Reduce the need to configure the same VLAN everywhere.
VTP Modes Link to heading
- VTP Servers are responsible for creating, deleting, or modifying entries in the VLAN database. Each VTP domain must have at least one VTP server, and this is the default mode for Cisco switches.
- VTP Clients cannot modify the VLAN database, and rely on advertisements from other switches to update its VLAN information.
- VTP Transparent switches maintain its own local VLAN database and ignore
all remote VTP messages.
- With VTP version 1[2], the transparent switch allows VTP advertisements from the same [any] VTP domain to pass through itself.
- Normal range VLAN configurations are stored both in flash:vlan.dat file and running-config. Extended range VLANs configurations are stored in the flash:vlan.dat if the switch is running VTP version 3; otherwise, they are stored in the running-config.
- A switch in VTP Off mode functions in the same manner as a VTP
transparent switch, except that it does not forward VTP advertisements on
trunks.
- Only available on switches that support VTP version 3, although it is not necessary to run VTP version 3 on the switch to be able to put it into VTP Off mode.
VTP Versions Link to heading
However, do not enable other VTP version on a network device unless all of the network devices in the same VTP domain are version 2/3-capable. When you enable VTP version 2/3 on a network device, all of the version 2/3-capable network devices in the domain enable VTP version 2/3.
VTP version 3:
- Hides the VTP password as the output of the
show vtp passwordcommand. - Propagates information about both normal- and extended-range VLANs.
- Only supports pruning for normal-range VLANs.
- Supports propagating private VLAN information. As with extended-range VLANs, the lack of PVLAN support in VTP version 2 required that all switches be in Transparent mode and manually configured at each switch.
- Supports opaque databases, meaning that it can transport more than just the VLAN database between switches (e.g. MSTP database).
- Provides protection from the false database accidentally being inserted into a
VTP domain by introducing the “primary server” mode.
- In VTP version 3, only the primary server is allowed to make changes to the domain.
- This means that if a switch with a higher revision number is added to the network, it will not overwrite the VLAN database of other switches in the domain unless it is the primary server.
- This reduces the risk of unintended changes and increases availability.
- A secondary server can only back up the updated VTP configuration received from the primary server in the NVRAMs.
VTP Advertisements – Revision Number Link to heading
There are three VTP messages:
- Advertisement request (client or server request)
- Subset advertisement (server response to an advertisement)
- Summary advertisement (server sends out every 5 minutes)
If the switch receives a VTP advertisement over a trunk link, it inherits the management domain name and the VTP configuration revision number.
- If a password is set, VTPv2 will not allow other switches to automatically learn the domain name.
The switch ignores advertisements with a different management domain name or an earlier configuration revision number.
- Any change to the VLAN database increments the configuration revision number by 1.
- Thus, a higher number represents a newer database revision.
While only VTP servers can change the VLAN database, VTP clients can advertise updates, to other clients and even to a server!
As long as the revision number is higher, the switch will accept the update.
This can result in a newly-introduced switch advertising a blank or incorrect VLAN database to all other switches in the domain. Switch ports would then lose their VLAN memberships, resulting in a significant network outage.
This can be avoided when implementing a new switch into the VTP domain.
There are two methods of resetting the revision number to zero on a switch:
- Change the VTP domain name, and then change it back to the original name.
- Change the VTP mode to transparent, and then change it back to either server or client. Transparent switches always has a revision number of 0.
VTP Configuration Link to heading
| Task | IOS Command |
|---|---|
| Change VTP domain name | Switch(config)# vtp domain domain-name |
| Configure VTP mode | Switch(config)# vtp mode {server/client/transparent} |
| Configure VTP password | Switch(config)# vtp password password |
| Switch to another VTP version | Switch(config)# vtp version {1/2/3} |
VTP Pruning Link to heading
Since a L2 switch belongs to only one broadcast domain, it will forward both broadcasts and multicasts out every port in the same VLAN but the originating port. This includes sending out broadcasts out trunk ports to other switches, which will in turn flood that broadcast out all ports in the same VLAN.
- Thus, broadcasts are only sent out the necessary trunk ports where those VLANs exist, eliminating unnecessary broadcast or multicast traffic.
- VTP pruning is disabled by default on IOS switches. It must be enabled on a server, and will be applied globally to the entire VTP domain (servers and clients).
- Transparent mode switches require manually pruning inactive VLANs off their trunk links.
| Task | IOS Command |
|---|---|
| Enable dynamic VTP pruning | Switch(config)# vtp pruning |
| Select an interface (port) to configure | Switch(config)# interface interface_# |
| Manually specify which / the list of VLANs to be pruning eligible on a trunk link | Switch(config-if)# switchport trunk pruning vlan {vlan-list all / none [add / except / none / remove {vlan-list}]} |
VTP Verification Link to heading
| Task | IOS Command |
|---|---|
| View status information about VTP | Switch# show vtp status |
| View VTP statistical information and error counters | Switch# show vtp counters |
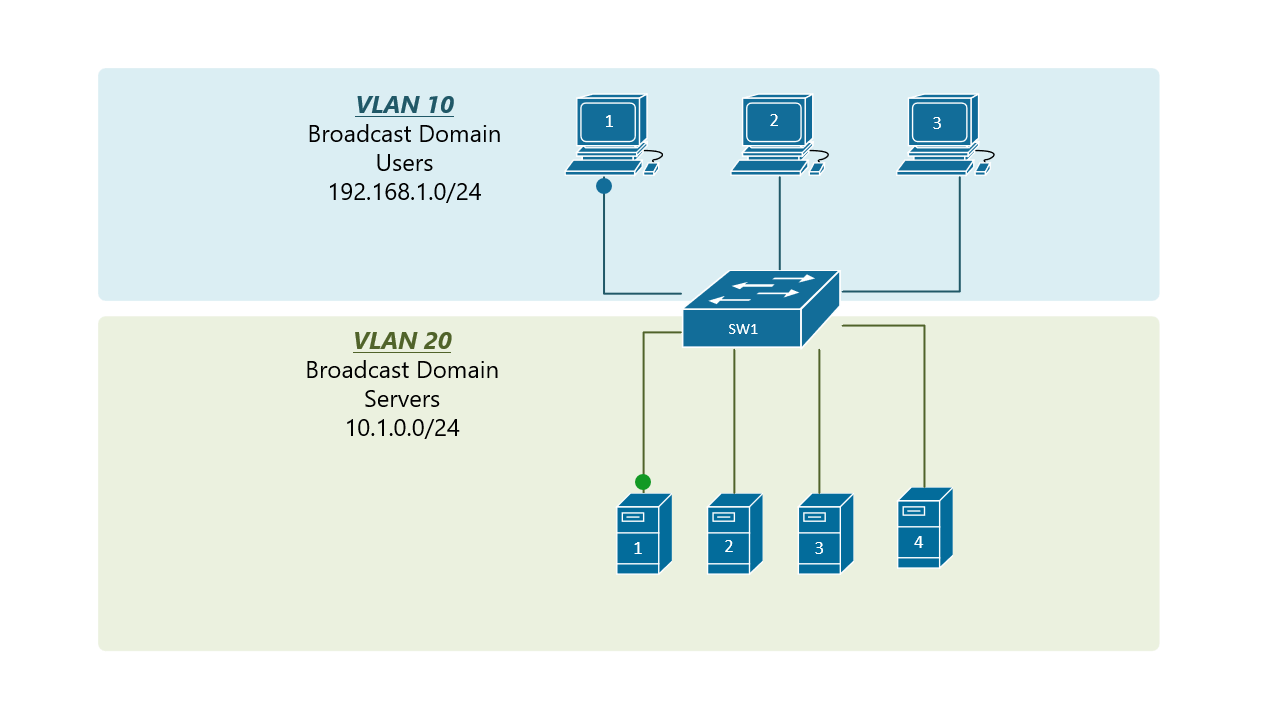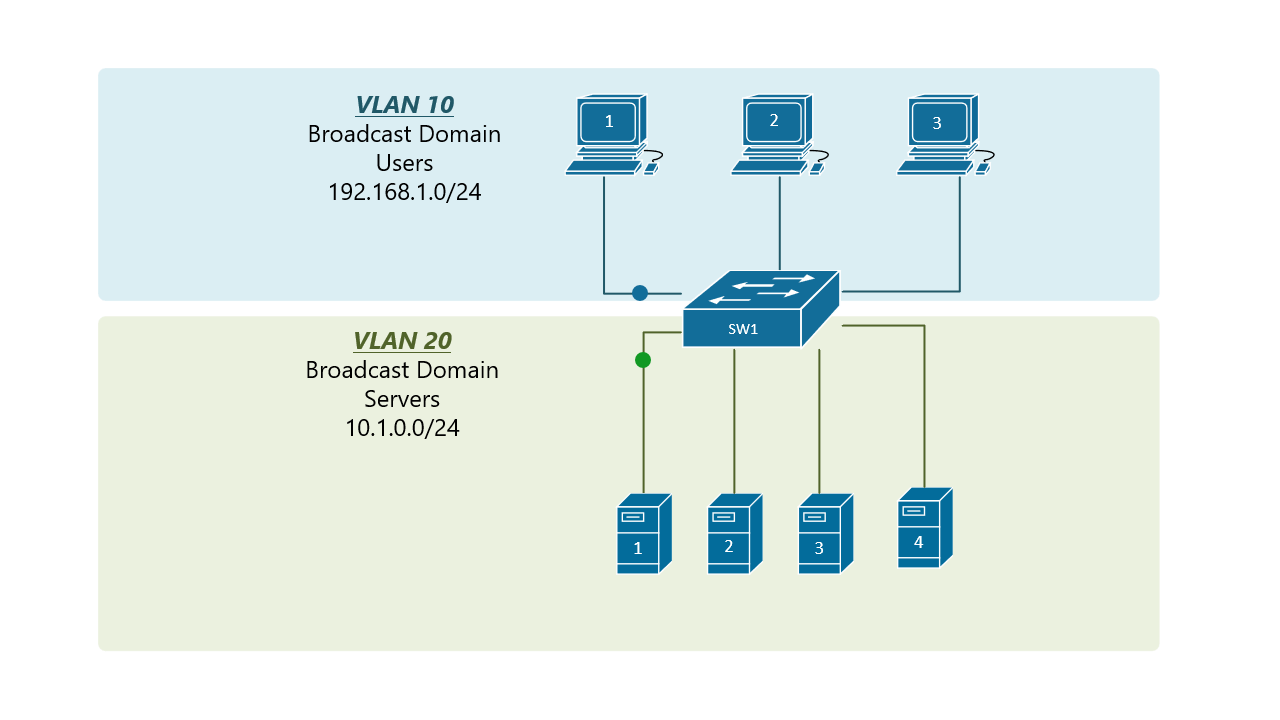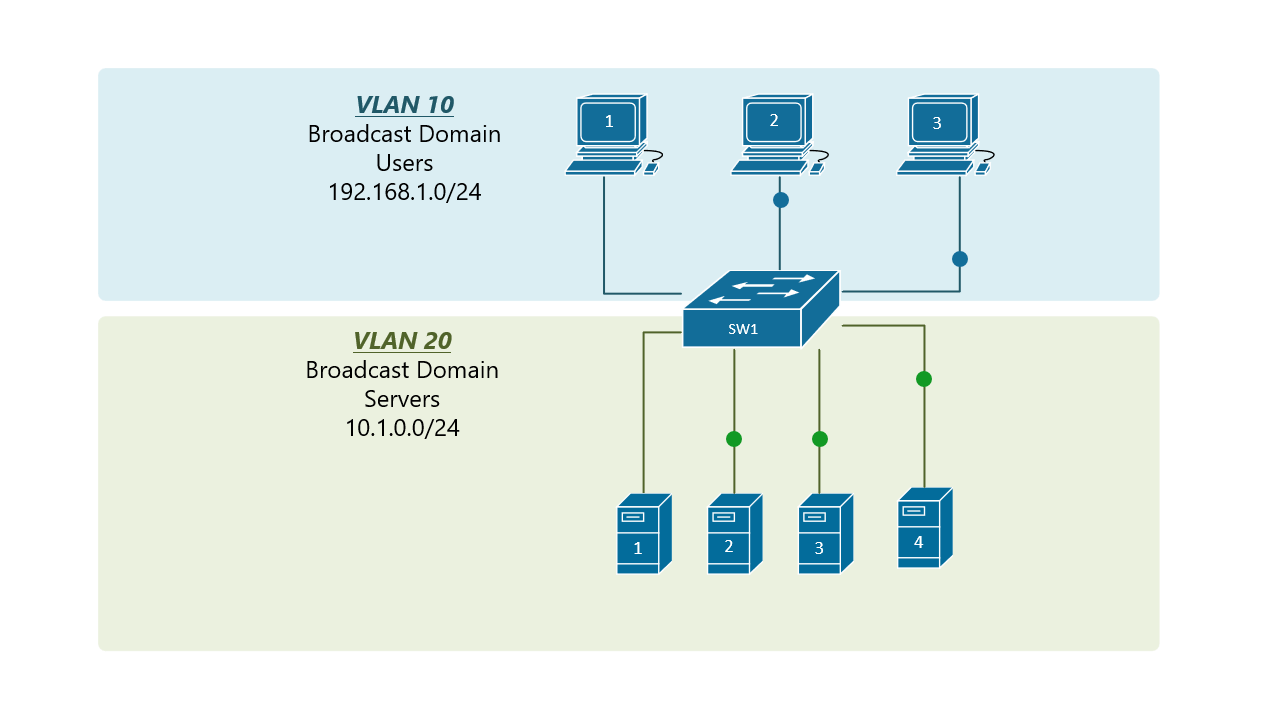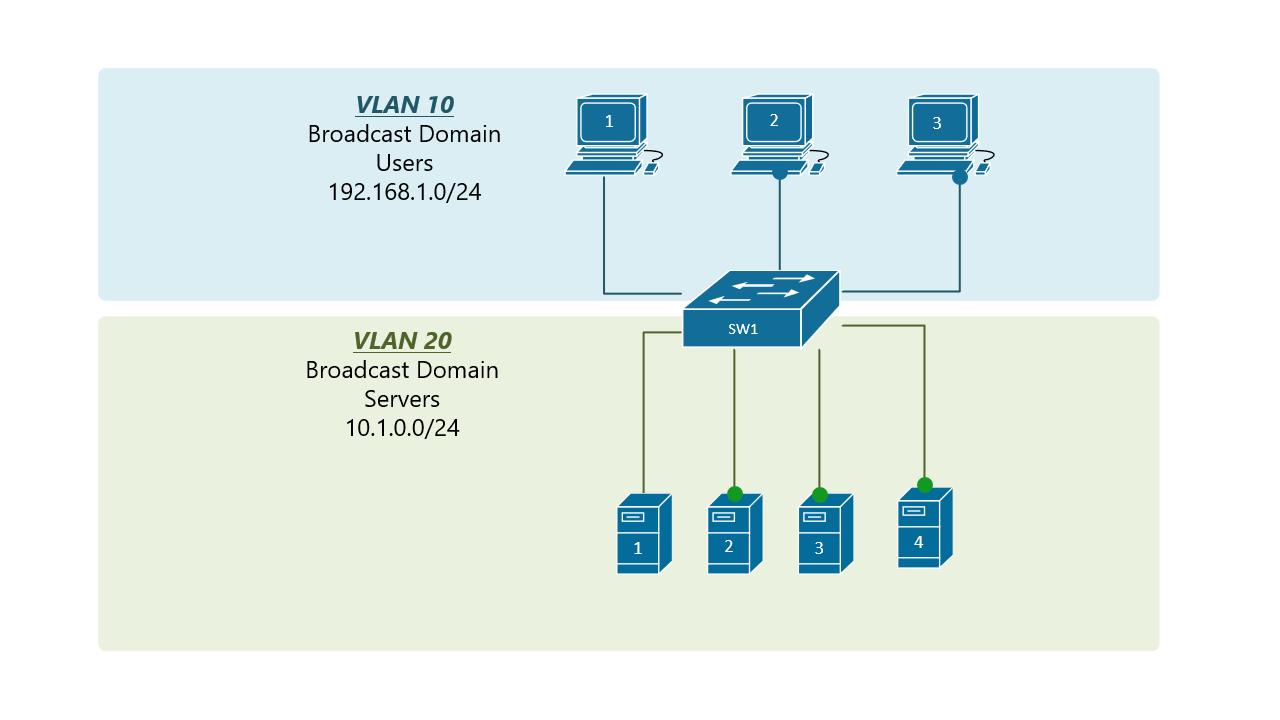
Before and After VLAN Implementation Link to heading
PC1 sends out a local Layer 2 broadcast. The switches forward the broadcast frame out all available ports.
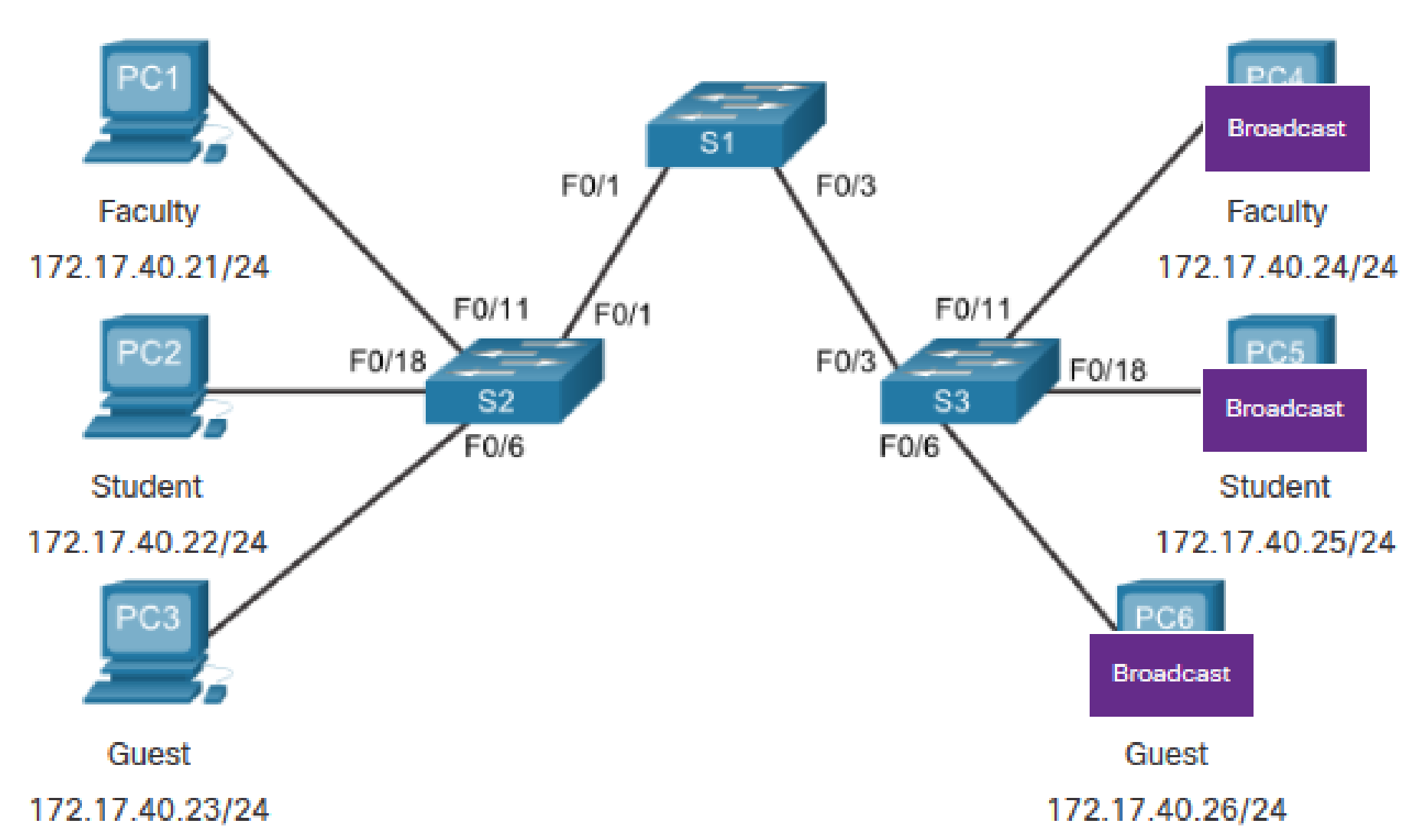
PC1 sends out a local Layer 2 broadcast. The switches forward the broadcast frame only out ports configured for VLAN 10.
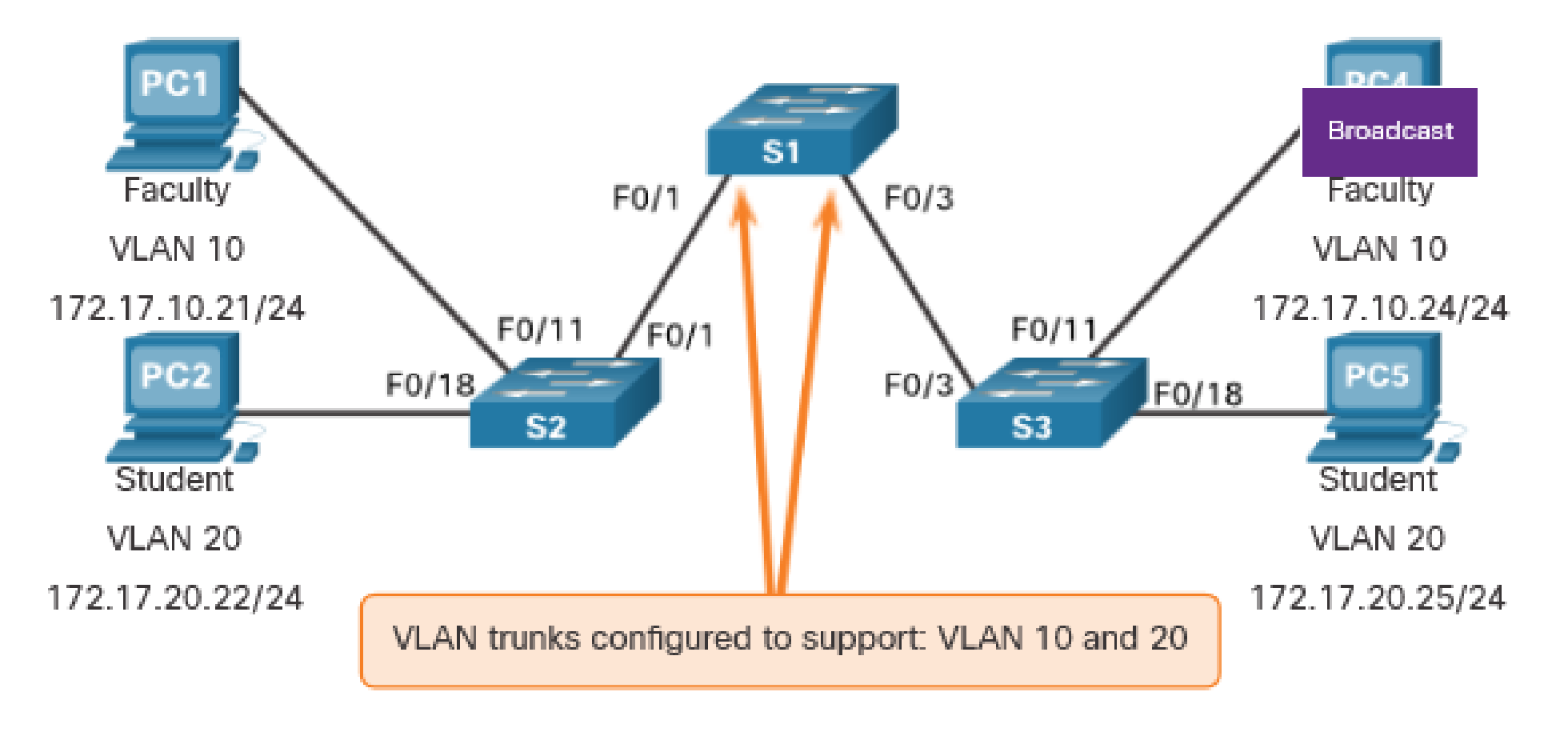
Communicating with a device in the same VLAN is called intra-VLAN communication.
VLAN Limits Link to heading
| Normal Range VLAN 1 – 1005 | Extended Range VLAN 1006 - 4095 |
|---|---|
| Used in small-to-medium-sized businesses | Used by service providers |
| 0 (all-zero tag), 1002 – 1005 are reserved for legacy VLANs | 4095 (all-one tag) is reserved |
| 1, 1002 – 1005 are auto-created and cannot be deleted | Support fewer VLAN features |
| Configurations stored in running-config (VTP v1) or flash:vlan.dat (VTP v2/3) | Stored in running-config (VTP v1/2) or flash:vlan.dat (VTP v3) |
| VTP can synchronise between switches | Require VTP configurations |
802.1Q Tagging Method Link to heading
- FCS has to be recalculated when adding and removing the tag from a frame.
- The tag is removed before sending to non trunk ports.
- The native VLAN contains untagged frames, even on trunk connections.
Cisco IOS Commands Link to heading
VLAN Creation Link to heading
| Task | IOS Command |
|---|---|
| Create a VLAN with a valid ID number | Switch(config)# vlan vlan_# |
| Specify a unique name to identify the VLAN | Switch(config-vlan) name vlan-name |
VLAN Access Port Configuration Link to heading
| Task | IOS Command |
|---|---|
| Select an interface (port) to configure | Switch(config)# interface interface_# |
| Configure that port as an access port | Switch(config-if)# switchport mode access |
| Assign a VLAN to the access port | Switch(config-if)# switchport access vlan vlan_# |
Voice VLAN Configuration Link to heading
| Task | IOS Command |
|---|---|
| Select an interface (port) to configure | Switch(config)# interface interface_# |
| Configure that port as an access port | Switch(config-if)# switchport mode access |
| Assign a VLAN to the access port | Switch(config-if)# switchport access vlan vlan_# |
| Configure prioritisation of voice traffic over other traffic | Switch(config-if)# mls qos trust cos |
| Assign a voice VLAN to the access port | Switch(config-if)# switchport voice vlan vlan_# |
VLAN Verification Link to heading
| Task | IOS Command |
|---|---|
| Display VLAN name, status, and its ports one VLAN per line | Switch# show vlan brief |
| Display information about the identified VLAN ID number | Switch# show vlan id vlan_# |
| Display information about the identified VLAN name | Switch# show vlan name vlan-name |
| Display a count of the number of existing VLANs | Switch# show vlan summary |
VLAN Access Port Reassignment and Deletion Link to heading
- It is possible to simply reassign a port by entering into the interface configuration mode and changing it using the switchport access vlan vlan_# command.
- You can also use no switchport access vlan to place the interface back in VLAN 1.
- Before deleting a VLAN, ensure all ports are assigned to a different VLAN. If they are not they will not appear on the show vlan brief screen and need to be reset via the no switchport access vlan interface configuration command.
- Remove a VLAN from the vlan.dat file using the no vlan vlan_# command.
- You may also delete all previously configured VLANs using delete
flash:vlan.dat
- The switch must be reloaded after this is executed.
Trunk Links Configuration Link to heading
- Trunk links are configured differently to access ports. They are layer 2 and carry traffic for multiple VLANs.
- After configuring access ports, you need to establish trunking between all switches in order for the switches to forward the frame as the ports connecting the switches are assigned to VLAN 1 by default.
- By default, all active VLANs are allowed to traverse a trunk link.
- The trunk port takes about a short time to become active due to Spanning Tree Protocol.
- The native VLAN must be configured identically on both sides of the 802.1Q trunk, otherwise the switches will not form a trunk connection and spanning tree loops might result..
| Task | IOS Command |
|---|---|
| Select an interface (port) to configure | Switch(config)# interface interface_# |
| Set the access port to trunking mode | Switch(config-if)# switchport mode trunk |
| Assign the native VLAN (other than VLAN 1) to the access port | Switch(config-if)# switchport trunk native vlan vlan_# |
| Specify which / the list of VLANs to be allowed on the trunk link | Switch(config-if)# switchport trunk allowed vlan {vlan-list all / none [add / except / none / remove {vlan-list}]} |

S1(config)# interface range f0/1,f0/3
S1(config-if)# switchport mode trunk
S1(config-if)# switchport trunk native vlan 99
S2(config)# interface f0/1
S2(config-if)# switchport mode trunk
S2(config-if)# switchport trunk native vlan 99
S3(config)# interface f0/3
S3(config-if)# switchport mode trunk
S3(config-if)# switchport trunk native vlan 99
To explicitly allow a subset of VLANs on a trunk port:
Switch(config)# interface f0/1
Switch(config-if)# switchport trunk allowed vlan 3,9,11-15
The above command will force the trunk link to only forward traffic from VLANS 3, 9, and 11 – 15.
To remove a VLAN from the allowed list:
Switch(config)# interface f0/1
Switch(config-if)# switchport trunk allowed vlan remove 12
To add a specific VLAN back into the allowed list:
Switch(config)# interface f0/1
Switch(config-if)# switchport trunk allowed vlan add 25
To allow all VLANs except for a specific range:
Switch(config-if)# switchport trunk allowed vlan except 50-99
To allow all VLANs again:
Switch(config-if)# switchport trunk allowed vlan all
Trunking Verification Link to heading
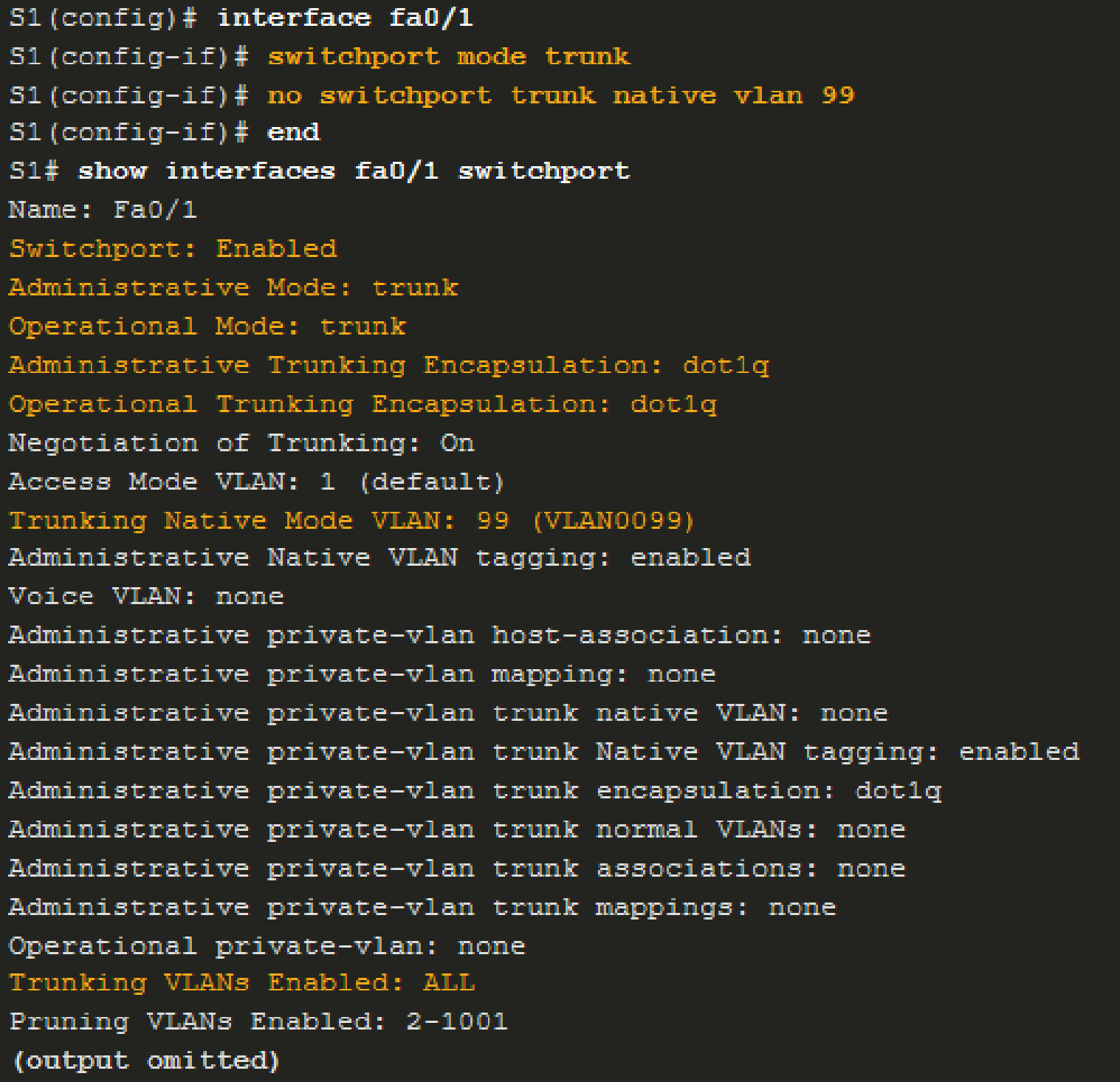
- The show interfaces interface_# switchport command determines
whether an interface is an access or trunk port.
- It also shows the trunking state, encapsulation type, native VLAN, and VLANs allowed on the trunk.
- Useful for troubleshooting trunking issues.
- The show interface_# trunk command verifies if a trunk interface
exists.
- If there are no interfaces in an active trunking state, this command will return no output.
Dynamic Trunking Protocol (DTP) Link to heading
- Proprietary Cisco protocol.
- Turned off using the switchport nonegotiate interface command.
- Turned on using the switchport mode dynamic auto interface command.
- DTP is vulnerable to a security risk, allowing an attacker to hop to another
by switch spoofing.
- Read more at 🔗.
- Cisco routers do not talk DTP.
Port Modes Link to heading
| Port Mode | Function |
|---|---|
| access | Puts the LAN port into permanent nontrunking (access) mode and negotiates to convert the link into a nontrunk (access) link. It says: “Never trunk on this end, and I will send out DTP to help my link partner reach the same conclusion.” |
| trunk | Puts the LAN port into permanent trunking mode and negotiates to convert the link into a trunk link. It says: “Always trunk on this end, and I will send DTP to attempt to negotiate a trunk on the other end.” |
| dynamic desirable | Puts the LAN port into trunking mode if the neighbouring LAN port is set to trunk, dynamic desirable, or dynamic auto mode. It says: “Ask the other end to trunk using DTP and trunk if the negotiation succeeds. If DTP negotiation fails, then become an access port.” |
| dynamic auto (default) | Puts the LAN port into trunking mode if the neighbouring LAN port is set to trunk or dynamic desirable mode. It says: “If the other end asks me to be a trunk with DTP, then become a trunk, but I wont initiate any negotitation from this end. If no one asks me to become a trunk then I will become an access port.” |
switchport nonegotiate puts the LAN port into permanent trunking mode but
disables DTP (do not send or respond to DTP from this end)Encapsulation Methods Link to heading
switchport trunk encapsulation says: “Do not negotiate the trunk protocol with
DTP. Only use the trunk protocol specified in this command (isl or dot1q).”| Encapsulation Method | Function |
|---|---|
switchport trunk encapsulation isl | Specifies ISL encapsulation on the trunk link |
switchport trunk encapsulation dot1q | Specifies 802.1Q encapsulation on the trunk link |
switchport trunk encapsulation negotiate | Specifies that the LAN port negotiate with the neighbouring LAN port to become an ISL (preferred) or 802.1Q trunk, depending on the configuration and capabilities of the neighbouring LAN port |
DTP Negotiation Link to heading
In the following table, the arguments for the switchport mode command are listed vertically for the local side of the link and horizontally for the remote side of the link.
The intersection point indicates whether the link will transition to access mode or trunk mode after the two switches have exchanged DTP messages.
| Administrative Mode | Dynamic Auto | Dynamic Desirable | Trunk | Access |
|---|---|---|---|---|
| Dynamic Auto | Access | Trunk | Trunk | Access |
| Dynamic Desirable | Trunk | Trunk | Trunk | Access |
| Trunk | Trunk | Trunk | Trunk | Limited connectivity |
| Access | Access | Access | Limited connectivity | Access |
DTP Delay Link to heading
switchport mode trunk + switchport nonegotiate +
switchport trunk encapsulation for the fastest possible formation of a trunk.DTP Spoofing Link to heading
DTP is not secure in that a device could send false DTP packets and cause a switchport to become an unauthorised trunk port, giving the attacker access to all VLANs allowed on that trunk.
Therefore, the best practice is to set the mode statically and deactivate the
DTP protocol on a port using the command switchport nonegotiate (this command
is necessary only for trunk ports).
VLAN Design Best Practices Link to heading
- Cisco recommends the use of IEEE 802.1Q as the trunk protocol. Cisco ISL is obsolete.
- Move all ports away from VLAN 1.
- Restrict VLAN 1 to serving as a conduit only for L2 control traffic (such as CDP or VTP), supporting no other traffic.
- Create a not-in-use VLAN (black hole) for all unused switch ports and shut down all of them.
- Define a native/black hole VLAN to be a dummy (disabled/unused) VLAN distinct from all other VLANs defined in the switched LAN.
- Change the management VLAN to a distinct VLAN. Do not use VLAN1.
- Ensure only devices in the management VLAN can SSH to the switch.
- Separate management and user traffic.
- Allow only the required, necessary VLANs over a trunk.
- Force trunk ports to tag native VLAN traffic.
- Manually configure trunk ports (set to nonegotiate) to avoid DTP negotiation errors.
- Avoid automatic pruning of VLANs on trunk interfaces. Prune unused/inactive VLANs with manual configuration to avoid broadcast propagation.
- Use VTP Transparent mode because there is little need for a common VLAN database in hierarchical networks.