Table of Contents Link to heading
- Media Access Control (MAC) Address Flooding
- Dynamic Host Configuration Protocol (DHCP) Spoofing
- Discovery Protocol Information Leakage
- Telnet Attacks
- Security Best Practices
Media Access Control (MAC) Address Flooding Link to heading
A MAC address a standardised Data Link Layer address that is required for every port of devices that connect to a LAN. Other devices in the network use these addresses to locate specific ports in the network and to create and update routing tables and data structures. MAC addresses are 6 bytes long and are controlled by the IEEE.
- A malicious actor generates many Ethernet frames with random MAC addresses to fill up the MAC address table on the switch.
- When the MAC address table on the switch reaches its capacity, the switch will not be able to look up in the MAC address table any more and will instead flood all frames received out all ports, except the ingress port.
- This can be mitigated using port security to limit the number of MAC addresses allowed per port.
Enabling Port Security Link to heading
- Set the interface into trunk or access mode, depending on what is required.
- By default, L2 ports are set to dynamic auto and must be manually configured for port security to be enabled.
- Enable port-security using the
switchport port-securityinterface configuration command.
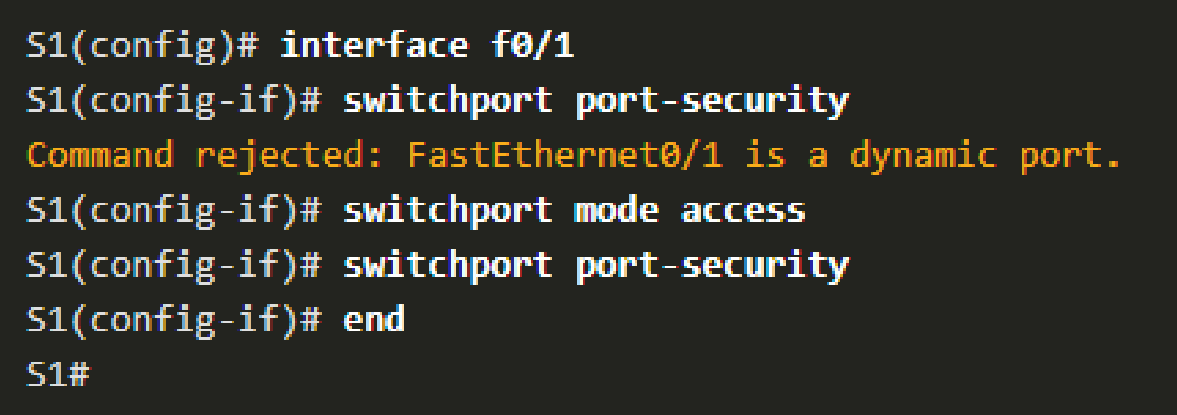
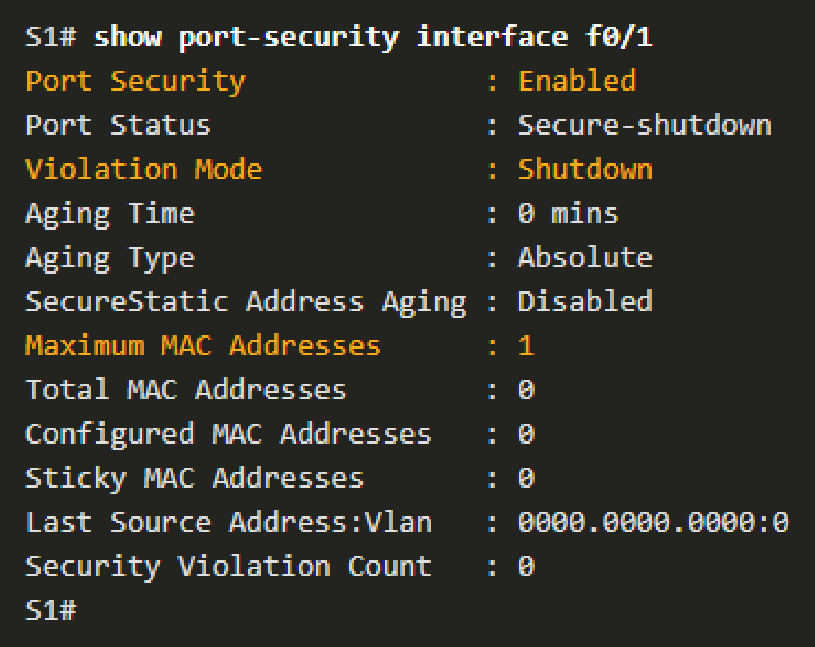
- Verify with the
show port-security interfacecommand. - By default, 1 MAC address is allowed on the port and is learned through the device connected to the port.
- By default, the violation mode is shut down.
- If more than one is learned, the port will transition to the error-disabled state.
Adjusting Port Security Link to heading
- To change the max number of MAC addresses allowed on a port simply use:
Switch(config-if)# switchport port-security maximum value
- Use the question mark keyword in the IOS to examine how many can be allowed on a particular switch.
- Manually Configured: the administrator must configure static MAC addresses
on the port.
Switch(config-if)# switchport port-security mac-address mac-address
- Dynamically Learned: the default operation method as described previously.
- Dynamically Learned – Sticky: learn and “stick” them to the running
config. Saving the running config will commit dynamically learned MAC
addresses to NVRAM.
Switch(config-if)# switchport port-security mac-address sticky
Port Security Aging Link to heading
Can be used to set the aging time for static and dynamic secure addresses on a port.
- Two types of aging are supported on a switch:
- Absolute – deleted after the specified aging time.
- Inactivity – deleted if they are inactive for a specified time.
- Useful when you wish to remove secure addresses without manual removal.
- Aging of statically configured secure addresses can be enabled or disabled on a per-port basis.
- Use the
switchport port-security agingcommand to enable or disable static aging for the secure port or to set the aging time or type.
Port Security Violation Modes Link to heading
- When a port security violation occurs, the port transitions into the error-disabled mode and takes specific actions based on the violation mode set.
- A violation occurs when the device connected does not match the addresses stored and the maximum allowed has been reached.
Switch(config-if)# switchport port-security violation {shutdown | restrict | protect}
| Mode | Description |
|---|---|
| shutdown (default) | The port transitions to the error-disabled state immediately, turns off the port LED, and sends a syslog message. It increments the violation counter. When a secure port is in the error-disabled state, an administrator must re-enable it by entering the shutdown and no shutdown commands |
| restrict | The port drops packets with unknown source addresses until you remove a sufficient number of secure MAC addresses to drop below the maximum value or increase the maximum value. This mode causes the Security Violation counter to increment and generates a syslog message |
| protect | This is the least secure of the security violation modes. The port drops packets with unknown MAC source addresses until you remove a sufficient number of secure MAC addresses to drop below the maximum value or increase the maximum value. No syslog message is sent |
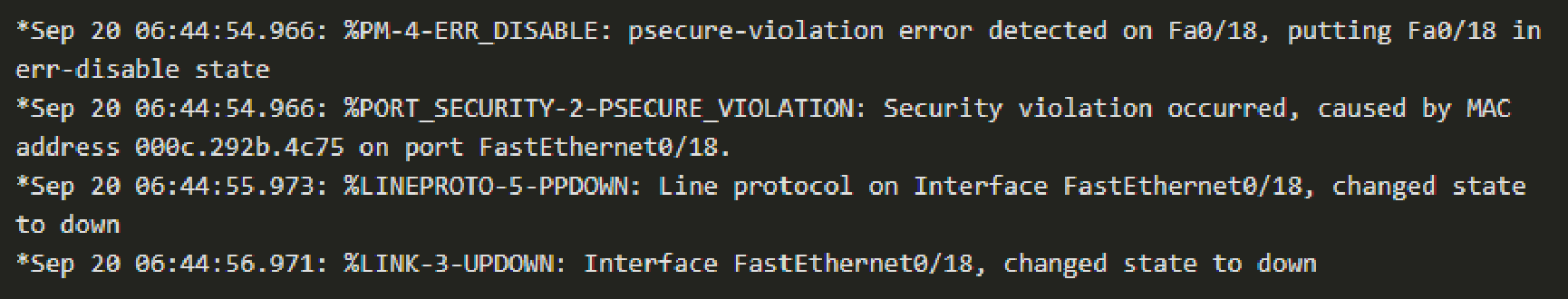
Ports in Error-disabled State Link to heading
- When a port is shut down and placed in the error-disabled state, no traffic is sent or received on that port.
- Several port-security related console messages appear in the console.
- The link state and port protocol are changed to down. A simple
no shutdownwill not recover the port. All related port LEDs are turned off. - To recover, first make sure you know what caused the violation and correct it
before issuing a
shutdownfollowed by ano shutdownon the interface.
Verifying Port Security Link to heading
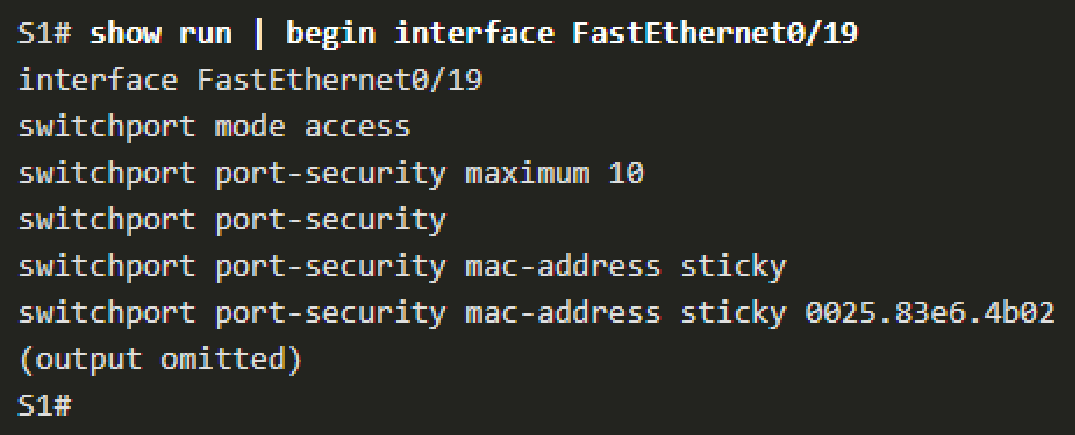
show runto verify sticky MAC addresses are sticking.
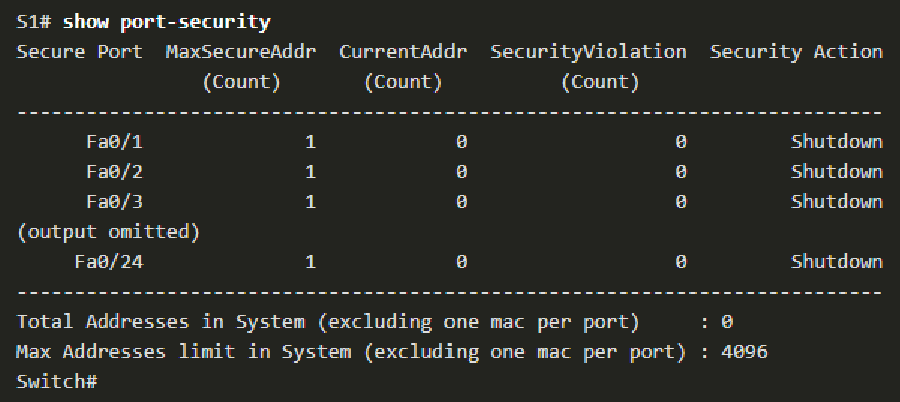
show port-securityto verify the port security is set correctly. More information can be retrieved by the show port-security interfacecommand.
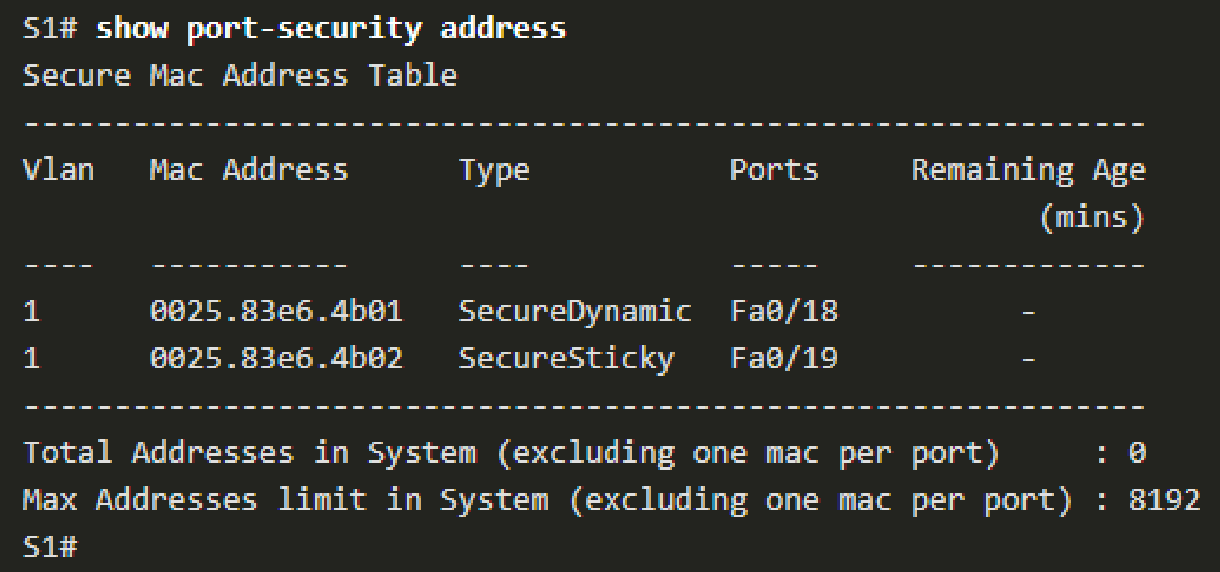
show port-security addresscan be used to verify all the secure MAC addresses that are manually configured or dynamically learned.
Dynamic Host Configuration Protocol (DHCP) Spoofing Link to heading
DHCP allows a host to obtain an IP address dynamically without the network administrator’s having to set up an individual profile for that machine.
- A malicious actor sets up a DHCP server on a network segment.
- A legitimate client broadcasts a request for DHCP configuration information.
- The rogue DHCP server responds before the legitimate DHCP server and gives the client the attacker-assigned IP configuration information (including the default gateway).
- By setting the client’s default gateway to the malicious actor’s IP address, it gives the malicious actor access to all packets that the client sends.
DHCP Starvation Link to heading
- Often used before a spoofing attack to deny service to the legitimate DHCP server.
- Aims to completely exhaust the DHCP pool available to legitimate clients.
- Makes use of tools (such as Gobbler) to constantly request new IP configurations for fake clients. Eventually depleting the pool available to legitimate clients.
- DHCP spoofing and starvation attacks can be mitigated by using DHCP snooping.
DHCP Snooping Link to heading
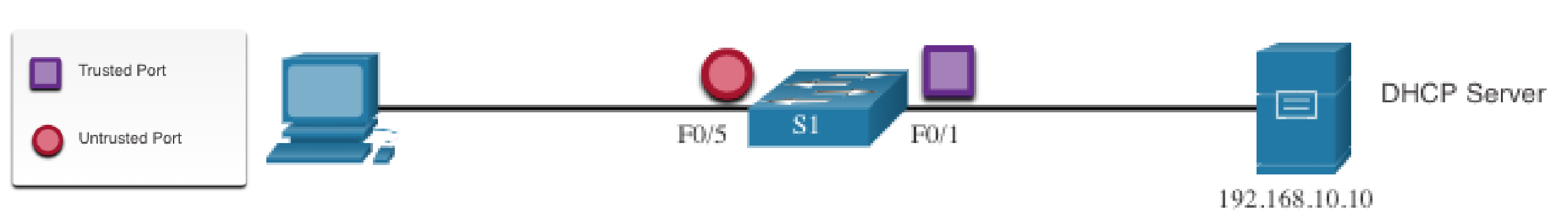
A security feature that acts like a firewall between untrusted hosts and trusted DHCP servers by filtering DHCP messages and rate-limits DHCP traffic on untrusted ports.
- A trusted port is:
- A device under administrative control, such as a switch, router, or server.
- An untrusted port is:
- All other ports on the switch that are not trusted, such as end devices.
- Manages a table called the DHCP snooping binding table which has an entry
for untrusted ports.
- Contains the source MAC and IP addresses assigned to the device by DHCP.
- Enable DHCP snooping globally using the
ip dhcp snoopingglobal configuration command. - Assign ports to trusted status by using the
ip dhcp snooping trustinterface configuration command (uplinks on the switch are often the trusted ports). - On all other ports (untrusted), limit the number of DHCP discovery messages
that can be received using the
ip dhcp snooping limit ratepackets- per-second interface configuration command.

Verifying DHCP Snooping Link to heading
show ip dhcp snoopingto verify DHCP snooping settings.show ip dhcp snooping bindingto view clients that have received DHCP information.

Discovery Protocol Information Leakage Link to heading
A discovery protocol, such as CDP, is used to discover other directly connected Cisco devices and to assist in Cisco IP Phone configuration. If an attacker is listening to CDP messages, it could learn important information about the device model and running IOS version and even voice VLAN information.
Telnet Attacks Link to heading
- Telnet is insecure and should be replaced by SSH immediately.
- General brute force password attacks and DoS attacks can impact Telnet.
- When a password is not known, an attacker can try every possible combination which is what a brute force attack is called. This can be tested against the device by using Telnet.
- In a Telnet DoS attack, the attacker exploits a flaw in the Telnet server software running on the switch that renders the Telnet service unavailable.
- This can be used in a coordinated attack to prevent an administrator from accessing devices during the breach.
- Vulnerabilities are patched through security patches included in newer IOS versions (however, this does not mean Telnet should be used).
Security Best Practices Link to heading
- Devise a security policy.
- Shut down unused services and ports.
- Use strong passwords.
- Control physical access to devices through physical security.
- Use HTTPS instead of HTTP.
- Use SSH instead of Telnet.
- Perform backup operations and have a plan for backups.
- Educate employees on different attack types, including Social Engineering.
- Encrypt and password-protect sensitive data, implement access controls as needed.
- Implement firewalls.
- Keep software up-to-date.