
Table of Contents Link to heading
- OSI Transport Layer
- Perspectives of Other Layers
- Roles of the Transport Layer
- Transmission Control Protocol (TCP)
- Properties
- Applications
- Example
- TCP Communication Process
- Datagram
- Source TCP Port Number (2 bytes)
- Destination TCP Port Number (2 bytes)
- Sequence Number (4 bytes)
- Acknowledgement Number (4 bytes)
- TCP Data Offset (4 bits)
- Reserved Data (3 bits)
- Control Flags (up to 9 bits)
- Window Size (2 bytes)
- TCP Checksum (2 bytes)
- Urgent Pointer (2 bytes)
- TCP Optional Data (0 to 40 bytes)
- User Datagram Protocol (UDP)
- Security Considerations
client and server are used as a reference for simplicity, but the
communication process can be initiated by any two hosts.OSI Transport Layer Link to heading
- Enable multiple applications to communicate over the network at the same time and manage the individual traffic streams over a single link.
- Ensure that, if required, all the data is received reliably and in order by the correct application.
Perspectives of Other Layers Link to heading
Applications do not need to know the operational details of the network in use. The applications generate data that is sent from one application to another, without regard to the destination host type, the type of media over which the data must travel, the path taken by the data, the congestion on a link, or the size of the network.
Additionally, the lower layers are not aware that multiple applications are sending data on the network. Their responsibility is to deliver pieces of data to the appropriate device. The transport layer then sorts these pieces before delivering them to the appropriate application.
Roles of the Transport Layer Link to heading
Identifying the Applications Link to heading
Each application process that needs to access the network is assigned an identifier (port number) unique in that host.
Segmenting Data Link to heading
Reassembling Segments Link to heading
Networks can provide multiple routes that can have different transmission times, so data can arrive in the wrong order.
Performing Flow Control Link to heading
It prevents the sender from overwhelming the receiver with too much data, which could cause buffer overflow and data loss.
| Layer | Responsibility |
|---|---|
| Transport | coordinate the data transfer between end-to-end hosts across different networks |
| Data link | coordinate the data transfer between adjacent nodes on the same network segment |
Enabling Error Recovery Link to heading
| Layer | Performed by | Responsibility |
|---|---|---|
| Transport | TCP | responsible for end-to-end delivery of segments across different networks |
| Data link | MAC sublayer | responsible for node-to-node delivery of frames on the same network segment |
Transmission Control Protocol (TCP) Link to heading
TCP is described in RFC 793.
Properties Link to heading
- Error recovery - use checksum to detect errors in the segments, acknowledgement to confirm the delivery of the segments, and retransmission to resend the missing or damaged segments.
- Flow control - use the sliding window mechanism to control the flow and congestion of data, and to improve the efficiency and throughput of data transmission.
- Session multiplexing - use port numbers to identify and multiplex different applications or services on a computer.
- Connection oriented - use a three-way handshake to establish and close a connection between two communicating devices.
Applications Link to heading
- Web browsing
- HTTP, HTTPS
- Ensure that the web pages are displayed correctly and completely
- E-mail
- SMTP , POP, IMAP
- Ensure that the emails are delivered without errors or loss
- File transfer
- FTP, SCP, SFTP
- Ensure that the files are transferred without corruption or interruption
- Remote access
- SSH, Telnet
- Ensure that the commands and data are transmitted reliably and securely
- Domain Name System (DNS)
- It mainly uses UDP, but it does use TCP for some large operations, such as zone transfers or large queries.
Example Link to heading
Applications, such as databases, web pages, and e-mail, require that all the sent data arrive at the destination in its original condition for the data to be useful. Any missing data could cause a corrupt communication that is either incomplete or unreadable. Therefore, these applications are designed to use TCP to ensure reliability. The additional network overhead is considered to be required for these applications.
TCP Communication Process Link to heading
TCP Server Processes Link to heading
When an active server application is assigned to a specific port, that port is considered to be “open” on the server. This means that the transport layer accepts and processes segments addressed to that port. Any incoming client request addressed to the correct socket is accepted, and the data is passed to the server application. There can be many simultaneous ports open on a server, one for each active server application.
TCP Three-Way Handshake Link to heading
Each side must receive the other side’s ISN and send a confirming acknowledgement (ACK) in a specific order.
It consists of three steps:
- SYN: One host initiates a connection by sending a SYN packet indicating its initial sequence number of x with a certain bit in the header set to indicate a connection request. This bit is set in the code field of the TCP header.
- SYN-ACK: The other host receives the packet, records the sequence number of x, replies with an acknowledgement of x + 1, and includes its own initial sequence number of y. The acknowledgement number of x + 1 means the host has received all octets up to and including x and is expecting x + 1 next.
- ACK: The initiating host responds with a simple ACK of y + 1 (the sequence number of the second host + 1), indicating it received the previous ACK, which finalises the connection process.
Because the second and third steps are combined in a single message, the exchange is called a three-way handshake/open connection.
Denial-of-Service (DoS) Attacks During Synchronization Link to heading
The attack process involves sending a large number of SYN segments to a target device, using spoofed or random source IP addresses, and never completing the handshake by sending the final ACK segment.
The effect of the attack is that the target device allocates memory and other resources for each half-open connection, and eventually runs out of capacity to handle new requests from legitimate users.
The possible countermeasures include limiting the number of half-open connections, using SYN cookies to verify the legitimacy of the SYN segments, and filtering out traffic from suspicious or known malicious sources.
TCP Two-Way Handshake Link to heading
Since each TCP connection represents two one-way communication sessions, to completely terminate a single TCP conversation, four exchanges are needed to end both sessions:
- FIN: When the client has no more data to send in the stream, it sends a segment with the FIN flag set.
- ACK: The server sends an ACK to acknowledge the receipt of the FIN to terminate the session from client to server.
- FIN: The server sends a FIN to the client, to terminate the server-to-client session.
- ACK: The client responds with an ACK to acknowledge the FIN from the server.
Datagram Link to heading
:max_bytes(150000):strip_icc():format(webp)/tcp-headers-f2c0881ea4c94e919794b7c0677ab90a.jpg)
Image Source: Lifewire
Source TCP Port Number (2 bytes) Link to heading
The source TCP port number represents the sending device.
Destination TCP Port Number (2 bytes) Link to heading
The destination TCP port number is the communication endpoint for the receiving device.
Sequence Number (4 bytes) Link to heading
Message senders use sequence numbers to mark the ordering of a group of messages, allowing the transport layer function on the destination host to reassemble segments in the order in which they were transmitted.
Acknowledgement Number (4 bytes) Link to heading
Both senders and receivers use the acknowledgement numbers field to communicate the sequence numbers of messages that are either recently received or expected to be sent.
TCP Data Offset (4 bits) Link to heading
The data offset field stores the total size of a TCP header in multiples of four bytes. A header not using the optional TCP field has a data offset of 5 (representing 20 bytes), while a header using the maximum-sized optional field has a data offset of 15 (representing 60 bytes).
Reserved Data (3 bits) Link to heading
Reserved data in TCP headers always has a value of zero. This field aligns the total header size as a multiple of four bytes, which is important for the efficiency of computer data processing.
Control Flags (up to 9 bits) Link to heading
TCP uses a set of six standard and three extended control flags - each an individual bit representing On or Off - to manage data flow in specific situations.
Window Size (2 bytes) Link to heading
Flow control is done by using the sliding window mechanism. For example, the receiver can use the window size field in the TCP header to indicate how much buffer space it has available for incoming data. The sender can then adjust its window size accordingly, and avoid sending more data than the receiver can handle or sending too little data and wasting bandwidth.
TCP Checksum (2 bytes) Link to heading
The checksum value inside a TCP header is generated by the protocol sender as a mathematical technique to help the receiver detect messages that are corrupted or tampered with.
Urgent Pointer (2 bytes) Link to heading
The urgent pointer field is often set to zero and ignored, but in conjunction with one of the control flags, it can be used as a data offset to mark a subset of a message as requiring priority processing.
TCP Optional Data (0 to 40 bytes) Link to heading
Usages of optional TCP data include support for special acknowledgement and window scaling algorithms.
User Datagram Protocol (UDP) Link to heading
UDP is described in RFC 768.
Properties Link to heading
- Unreliable - it does not guarantee the delivery, order, or integrity of the data.
- Connectionless - it does not establish or maintain a connection between the sender and the receiver.
- Simple and fast - it has a minimal header and no error recovery or flow
control mechanisms.
- It delivers data as it arrives, without waiting for acknowledgements or resending lost data.
- It does use a checksum to detect corrupt data in packets, but it does not attempt to correct them.
Applications Link to heading
It can also support multicast and broadcast communication.
- Domain Name System (DNS), Dynamic Host Configuration Protocol (DHCP),
and Network Time Protocol (NTP)
- It only consists of a single request and a single reply packet, so it will simply retry the request if it does not receive a response, and therefore they do not need TCP to guarantee the message delivery.
- Streaming media applications
- E.g., movies, music, or video conferencing
- They can handle some packet loss or out-of-order delivery, as long as the quality is acceptable.
- Online multiplayer games
- They need low latency and high speed, and can cope with some packet loss or duplication, as long as the game logic is consistent.
- Voice over IP (VoIP)
- It can deal with some packet loss or corruption, as long as the voice quality is not significantly affected.
- Trivial File Transfer Protocol (TFTP)
- It is mainly used for booting devices or updating firmware
- It relies on the application layer to handle any errors or losses.
- Simple Network Management Protocol (SNMP)
- UDP is suited for repetitive, low-priority functions like alarm monitoring.
Example Link to heading
Some applications are more tolerant of the loss of small amounts of data, such as real-time applications that require low latency and high speed. For example, if one or two segments of a video stream fail to arrive, it would only create a momentary disruption in the stream. This can appear as distortion in the image but might not even be noticeable to the user. Imposing overhead to ensure reliability for this application could reduce the usefulness of the application. The image in a streaming video would be greatly degraded if the destination device had to account for lost data and delay the stream while waiting for its arrival.
UDP Communication Process Link to heading
UDP Client Processes Link to heading
Because UDP does not create a session, as soon as the data is ready to be sent and the ports are identified, UDP can form the datagram and pass it to the network layer to be addressed and sent on the network.
UDP Server Requests Link to heading
When a UDP-based server application receives a datagram destined for one of the open ports, it forwards the application data to the appropriate application based on its port number.
Datagram Link to heading
UDP is low overhead because it has a smaller header and fewer control mechanisms compared to TCP.
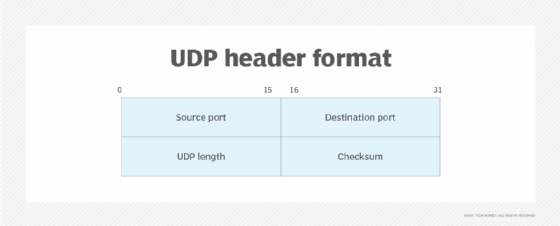
Image Source: Tech Target
Source Port (2 bytes) Link to heading
The source UDP port number represents the sending device.
Destination Port (2 bytes) Link to heading
The destination UDP port number is the communication endpoint for the receiving device.
Length (2 bytes) Link to heading
The length field in UDP represents the total size of each datagram, including both header and data. This field ranges in value from a minimum of 8 bytes—the required header size—to sizes above 65,000 bytes.
Checksum (2 bytes) Link to heading
Similar to TCP, a UDP checksum allows receivers to cross-check incoming data for any corrupted bits of the message, although it does not attempt to correct them.
Security Considerations Link to heading
One way to improve security on a server is to restrict server access to only those ports associated with the services and applications that should be accessible to authorised requestors.
Randomised source port numbers also help with security. If there is a predictable pattern for destination port selection, an intruder can more easily simulate access to a client by attempting to connect to the port number most likely to be open.
With regards to TCP sessions, there are three ways to add security to the data network, implemented either for all TCP sessions or only for selected sessions:
- Denying the establishment of TCP sessions
- Allowing sessions to be established for specific services only
- Allowing traffic only as a part of already established sessions