Table of Contents Link to heading
- Address Resolution Protocol (ARP)
- Displaying ARP Tables
- ARP Issues
- Reverse Address Resolution Protocol (RARP)
- Neighbour Discovery Protocol (NDP)
Address Resolution Protocol (ARP) Link to heading
Being ARP enabled, a host or router can dynamically learn the MAC address of another IP host or router on the same LAN.
Resolving IPv4 Addresses to MAC Addresses Link to heading
In a transmitting device, when an IPv4 packet is sent to L2 to be encapsulated into a frame, the device must identify the destination MAC address that is mapped to the destination IPv4 address.
To find this MAC address, the node refers to a table in its RAM memory called the ARP table or the ARP cache. Each entry, or row, of the ARP table has a pair of values: an IPv4 address and a MAC address. The ARP table caches the mapping for the devices on the local network.
To begin the process, a transmitting node attempts to locate in the ARP table the MAC address mapped to an IPv4 destination. If this map is cached in the table, the node uses the MAC address as the destination MAC in the frame that encapsulates the IPv4 packet. The frame is then encoded onto the networking media.
ARP Request Link to heading
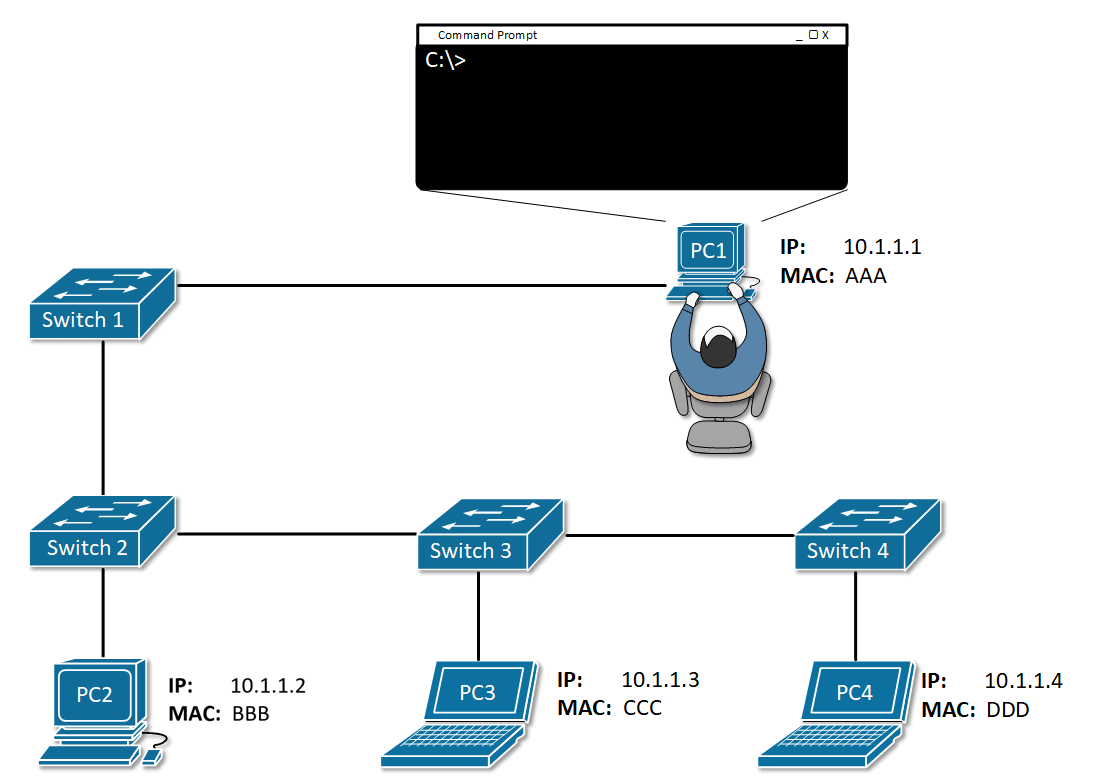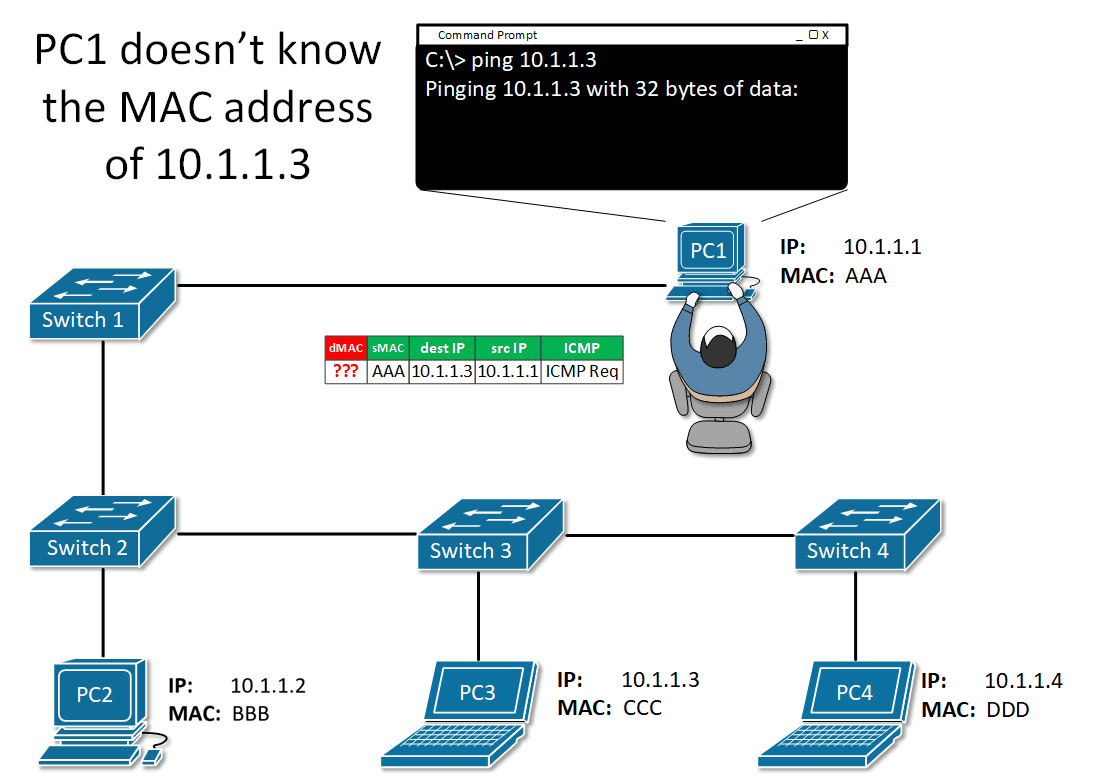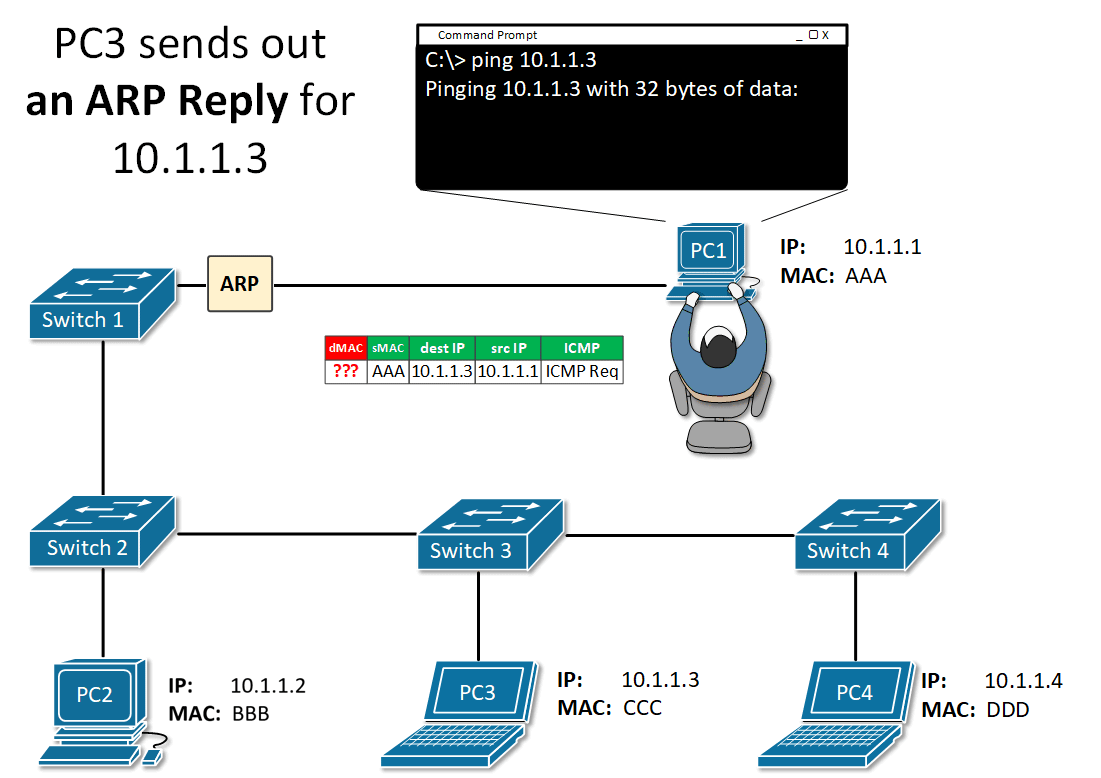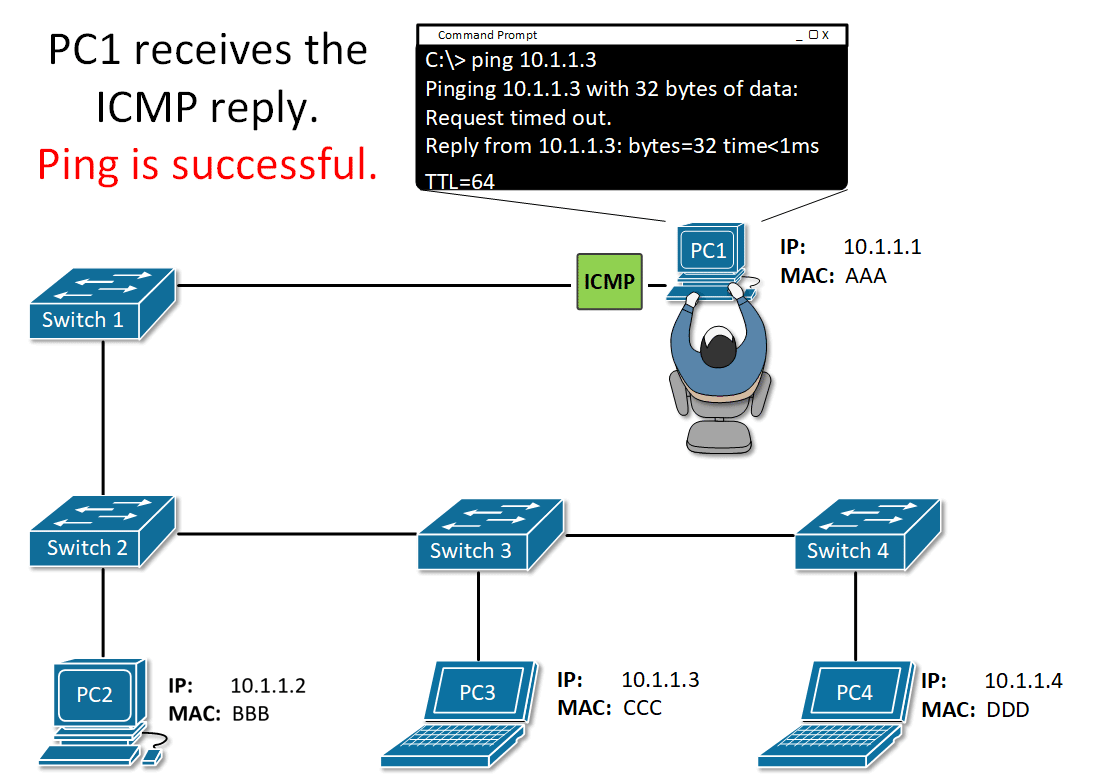
A broadcast message sent when a device needs a MAC address associated with an IPv4 address which it does not have an entry in its ARP table.
It is simply a request that reads: “if this is your IP address, please reply with your MAC address”.
The ARP request message includes:
- Target IPv4 address – The IPv4 address that requires a corresponding MAC address.
- Target MAC address - The unknown MAC address and will be empty in the ARP request message.
The ARP request is encapsulated in an Ethernet frame using the following header information:
- Destination MAC address – A broadcast address requiring all Ethernet NICs on the LAN to accept and process the ARP request (FF:FF:FF:FF:FF:FF).
- Source MAC address – The sender of the ARP request’s MAC address.
- Type - ARP messages have a type field of 0x806. This informs the receiving NIC that the data portion of the frame needs to be passed to the ARP process.
Since ARP requests are broadcasts, they are flooded out all ports by the switch except the receiving port. Every local Ethernet NIC must process the ARP request to see if the target IPv4 address matches its own. A router will not forward broadcasts out other interfaces.
Only one device on the LAN will have an IPv4 address that matches the target IP address in the ARP request. All other devices will not reply.
Scenario - Static IP Addressing Link to heading
When a local device (e.g. a PC) is statically assigned IP address (e.g. 192.168.1.10), in case that it does not have an entry for this IP address in the ARP table, it will broadcast an ARP request to determine if this address is available.
If there is no reply, the PC is successfully assigned “192.168.1.10”; otherwise, it will detect “an IP address confict” error.
ARP Reply Link to heading
The ARP reply message includes:
- Sender’s IPv4 address - The IPv4 address of the device whose MAC address was requested by the sender of the ARP request.
- Sender’s MAC address - The MAC address of the device whose IP address matches that of the sender of the ARP request.
The ARP reply is encapsulated in an Ethernet frame using the following header information:
- Destination MAC address - The MAC address of the sender of the ARP request.
- Source MAC address - The MAC address of the sender of the ARP reply .
- Type - ARP messages have a type field of 0x806. This informs the receiving NIC that the data portion of the frame needs to be passed to the ARP process.
Only the device that originally sent the ARP request will receive the unicast ARP reply. Once the ARP reply is received, the device will cache the mapping of IPv4 address and the corresponding MAC address in its ARP table. Packets destined for that IPv4 address can now be encapsulated in frames using its corresponding MAC address.
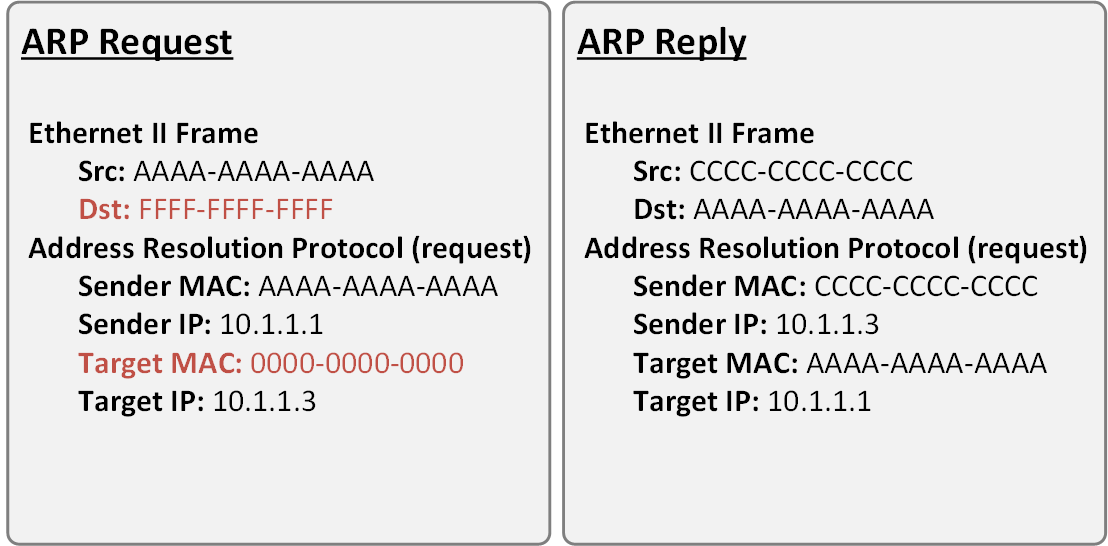
Image Source: Network Academy.
Maintaining a Cache of Mappings Link to heading
Populating to the ARP Table Link to heading
Dynamic Entries Link to heading
As a node receives frames from the media, it can record the source IPv4 and MAC address from the frame’s header as a mapping in the ARP table. As frames are transmitted on the network, the devices dynamically populates their ARP table with address pairs.
Entries learnt through the ARP request-reply processes are also dynamic entries.
Static Entries Link to heading
To add a static ARP entry:
Host(config)# arp ip_# mac _#
To remove a static ARP entry:
Host(config)# no arp ip_# mac _#
Getting the Map for a Frame Link to heading
When ARP receives a request to map an IPv4 address to a MAC address, it looks for the cached map in its ARP table. If an entry is not found, the encapsulation of the IPv4 packet fails and the L2 processes notify ARP that they need a map.
The ARP processes then broadcast an ARP request in order to create a new map. If no device responds to the ARP request, the packet is dropped because a frame cannot be created. This encapsulation failure is reported to the upper layers of the device. If the device is an intermediary device, like a router, the upper layers can choose to respond to the source host with an error in an ICMPv4 packet.
Mapping Destinations Link to heading
Within the Local Network Link to heading
Outside of the Local Network Link to heading
In the event that the gateway entry is not in the table, the normal ARP process will send an ARP request to retrieve the MAC address associated with the IPv4 address of the router interface.
Proxy ARP Link to heading
In these cases, the device sends ARP requests for IPv4 addresses that are not on the local network instead of requesting the MAC address associated with the IPv4 address of the gateway.
To provide a MAC address for these hosts, a router interface can use a proxy ARP to respond on behalf of these remote hosts. This means that the ARP cache of the requesting device will contain the MAC address of the gateway mapped to any IPv4 addresses not on the local network.
Using proxy ARP, a router interface acts as if it is the host with the IPv4 address requested by the ARP request. By “faking” its identity, the router accepts responsibility for routing packets to the “real” destination.
If proxy ARP is disabled on the router interface, these hosts cannot communicate outside of the local network. However, by default, Cisco routers have proxy ARP enabled on LAN interfaces.
Use Cases of Proxy ARP Link to heading
- When an older implementation of IPv4 cannot determine whether the destination host is on the same logical network as the source. In these implementations, ARP always sends ARP requests for the destination IPv4 address.
- When a host believes that it is directly connected to the same logical network as the destination host. This generally occurs when a host is configured with an improper mask.
- When a host is not configured with a default gateway. Proxy ARP can help devices on a network reach remote subnets without the need to configure routing or a default gateway.
Removing Entries from the ARP Table Link to heading
Each device uses ARP cache timers to remove ARP entries that have not been used for a specified period of time. The times differ depending on the device and its operating system. For example, some Windows operating systems store ARP cache entries for 2 minutes. If the entry is used again during that time, the ARP timer for that entry is extended to 10 minutes.
Commands can also be used to manually remove all or some of the entries in the ARP table. After an entry has been removed, the process for sending an ARP request and receiving an ARP reply must occur again to enter the map in the ARP table.
Displaying ARP Tables Link to heading
| Device | Command |
|---|---|
| Cisco router | show [ip] arp |
| Windows PC | arp –a |
ARP Issues Link to heading
Overhead on the Media Link to heading
On a typical business network, these broadcasts would probably have minimal impact on network performance. However, if a large number of devices were to be powered up and all start accessing network services at the same time, there could be some reduction in performance for a short period of time.
For example, if all students in a lab logged in to classroom computers and attempted to access the Internet at the same time, there could be delays. However, after the devices send out the initial ARP broadcasts and have learnt the necessary MAC addresses, any impact on the network will be minimised.
ARP Spoofing/Poisoning Link to heading
An attacker forges the MAC address of a device, and then frames can be sent to the wrong destination.
Manually configuring static ARP associations is one way to prevent ARP spoofing. Authorised MAC addresses can be configured on some network devices to restrict network access to only those devices listed.
Reverse Address Resolution Protocol (RARP) Link to heading
Devices using RARP require that a RARP server be present on the network to response to RARP requests.
Consider an example in which a source device wants to send data to another device. The source knows the destination’s MAC address but is unable to locate its IP address in the ARP table. Therefore, the source initiates a process called a RARP request, which helps it detect its own IP address. The device builds a RARP request packet, and sends it out on the network. To ensure that all devices see the RARP request on the network, the device uses a broadcast MAC address.