
Table of Contents Link to heading
- Network Address Translation (NAT)
- Operation
- Bidirectional versus Unidirectional NAT
- Types of Addresses
- Types of NAT
- Verifying NAT
- Debugging NAT
- Troubleshooting NAT
Network Address Translation (NAT) Link to heading
Operation Link to heading
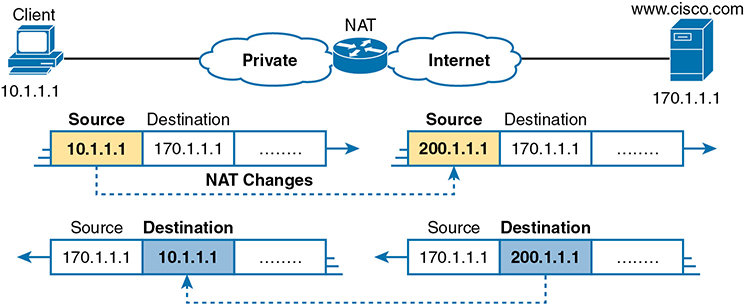
A host is using a private IP address is trying to communicate with a server on the Internet using a public IP address.
- When the host sends a packet to the server, the packet traverses a NAT-enabled router. The NAT replaces the host’s private address (10.1.1.1) in the source address field with a registered address (200.1.1.1) and forwards the packet.
- When the server sends a reply to the host, the destination address of the packet is “200.1.1.1”. This packet again traverses the NAT router, and the destination address is replaced with the host’s private address.
NAT is transparent to the end systems involved in the translation.
- The host knows only that its IP address is “10.1.1.1”; it is unaware of the “200.1.1.1” address.
- The server, on the other hand, thinks the address of the host is “200.1.1.1”; it knows nothing about the “10.1.1.1” address.
- On the other hand, the server’s real address is hidden from the host and therefore the host only thinks the server’s address is “170.1.1.1”.
Bidirectional versus Unidirectional NAT Link to heading
Bidirectional NAT features address translation from the inside network to the outside network as well as the translation of traffic flowing from the outside network to the inside network.
Unidirectional NAT occurs in one direction. For example, inside addresses being translated for outbound traffic, but no translation occurring for source addresses in the return path.
Types of Addresses Link to heading
An inside traffic comes from within the organisational network (a private enterprise or an ISP), whereas an outside traffic comes from an external network that is outside the organisational network (the public Internet or an Internet-facing service provider).
A local address is used while the packet flows in the local enterprise, whereas a global address is used while the packet flows in the global Internet.
Inside Local (IL) Link to heading
Inside Global (IG) Link to heading
Outside Local (OL) Link to heading
Because source NAT does not change this address, the term outside global applies at all times.
Outside Global (OG) Link to heading
This term is not used with source NAT.
Types of NAT Link to heading
Static NAT Link to heading
- Static NAT is bidirectional.
- A separate public address is required for every private address that requires static NAT addressing - a one-to-one mapping.
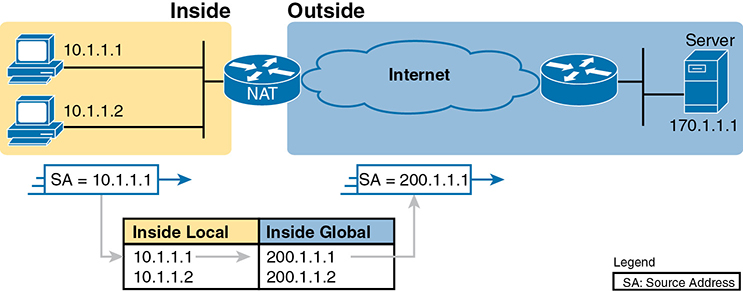
A data packet with the source address “10.1.1.1” in the left end, changes to the source address “200.1.1.1”, as it moves towards the right.
Configuration Link to heading
| Task | IOS Command |
|---|---|
| Configure interfaces to be in the inside part of the NAT design | Router(config-if)# ip nat inside |
| Configure interfaces to be in the outside part of the NAT design | Router(config-if)# ip nat outside |
| Configure the static mappings | Router(config)# ip nat inside source static inside_local inside_global |
Dynamic NAT Link to heading
- Like static NAT, the NAT router creates a one-to-one mapping between an IL and an IG, and changes the IP addresses in packets as they exit and enter the inside network.
- Dynamic NAT sets up a pool of possible IGs and defines matching criteria to determine which ILs should be translated with NAT.
A pool of five IGs has been established: “200.1.1.1” through “200.1.1.5”. NAT has also been configured to translate any ILs that matches “10.1.1.*”.
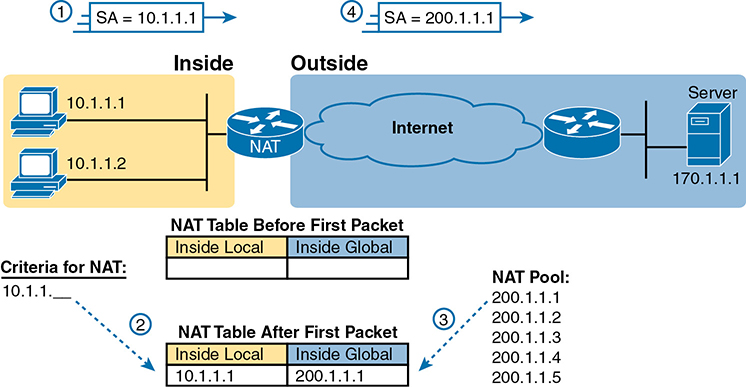
- Host 10.1.1.1 sends its first packet to the server at 170.1.1.1.
- As the packet enters the NAT router, the router applies some matching logic to decide whether the packet should have NAT applied. Because the logic has been configured to match source IP addresses that begin with 10.1.1, the router adds an entry in the NAT table for 10.1.1.1 as an inside local address.
- The NAT router needs to allocate an IP address from the pool of valid inside global addresses. It picks the first one available (200.1.1.1, in this case) and adds it to the NAT table to complete the entry.
- The NAT router translates the source IP address and forwards the packet.
Dynamic Entry Timeout Link to heading
To configure a timeout value that defines how long the router should wait,
having not translated any packets with that address, before removing the dynamic
entry:
Router(config)# ip nat translation timeout seconds
To clear a dynamic entry or all entries from the table:
Router(config)# clear ip nat translation {IP_# | *}
Exhausted Pooled Addresses Link to heading
The user must try again until a NAT entry times out, at which point the NAT function works for the next host that sends a packet. Essentially, the inside global pool of addresses needs to be as large as the maximum number of concurrent hosts that need to use the Internet at the same time.
Configuration Link to heading
| Task | IOS Command |
|---|---|
| Configure interfaces to be in the inside part of the NAT design | Router(config-if)# ip nat inside |
| Configure interfaces to be in the outside part of the NAT design | Router(config-if)# ip nat outside |
| Configure an ACL that matches the packets entering inside interfaces for which NAT should be performed | Router(config)# access-list acl_# {permit / deny} { host IP_# / network_IP_# subnet_mask} |
| Enable dynamic NAT | Router(config)# ip nat inside source list acl_# interface type/number overload |
NAT Overloading or Port Address Translation (PAT) Link to heading
Overloading is the solution to exhausted pooled addresses as it allows NAT to scale to support many clients with only a few public IP addresses.
PAT is an explicit mapping between an IP:Port to another IP:Port. Thus, PAT modifies both L3 and L4 headers while NAT only modifies the L3 header.
With overloading, instead of a one-to-one mapping, traffic is translated and given a unique outside port number to communicate with; in this situation, many internal hosts can be using the same outside address while utilising different port numbers.
Since the port number field has 16 bits, NAT overload can use more than 65,000 port numbers (one-to-65,000 mapping), allowing it to scale well without needing many registered IP addresses (in many cases, needing only one inside global IP address).
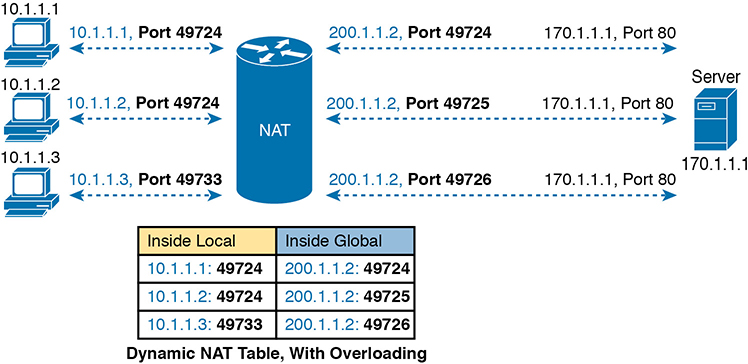
PAT takes advantage of the fact that, from a transport layer perspective, the server does not care whether it has one connection each to many different hosts or many connections to a single host IP address. It makes what looks like many TCP or UDP flows from different hosts look like the same number of flows from one host.
Configuration Link to heading
| Task | IOS Command |
|---|---|
| Configure interfaces to be in the inside part of the NAT design | Router(config-if)# ip nat inside |
| Configure interfaces to be in the outside part of the NAT design | Router(config-if)# ip nat outside |
| Configure an ACL that matches the packets entering inside interfaces for which NAT should be performed | Router(config)# access-list acl_# {permit / deny} { host IP_# / network_IP_# subnet_mask} |
| Configure the pool of public registered IP addresses | Router(config)# ip nat pool pool_name first_IP_# last_IP_# netmask subnet_mask |
| Enable dynamic NAT | Router(config)# ip nat inside source list acl_# pool pool_name |
Verifying NAT Link to heading
The show ip nat statistics lists the number of active entries and the number of hits which increments for every packet for which NAT must translate addresses.
Debugging NAT Link to heading
Troubleshooting NAT Link to heading
- Reversed inside and outside: Ensure that the configuration includes the ip nat inside and ip nat outside interface subcommands and that the commands are not reversed (the ip nat inside command on outside interfaces, and vice versa). With source NAT, only the inside interface triggers IOS to add new translations, so designating the correct inside interfaces is particularly important.
- Static NAT: Check the ip nat inside source static command to ensure it lists the inside local address first and the inside global IP address second.
- Dynamic NAT (ACL): Ensure that the ACL configured to match packets sent by the inside hosts match that host’s packets before any NAT translation has occurred. For example, if an inside local address of 10.1.1.1 should be translated to 200.1.1.1, ensure that the ACL matches source address 10.1.1.1, not 200.1.1.1.
- Dynamic NAT (pool): For dynamic NAT without PAT, ensure that the pool has enough IP addresses. When not using PAT, each inside host consumes one IP address from the pool. A large or growing value in the second misses counter in the show ip nat statistics command output can indicate this problem. Also, compare the configured pool to the list of addresses in the NAT translation table (show ip nat translations). Finally, if the pool is small, the problem may be that the configuration intended to use PAT and is missing the overload keyword (see the next item).
- PAT: It is easy to forget to add the overload option on the end of the ip nat inside source list command. PAT configuration is identical to a valid dynamic NAT configuration except that PAT requires the overload keyword. Without it, dynamic NAT works, but the pool of addresses is typically consumed very quickly. The NAT router will not translate nor forward traffic for hosts if there is not an available pool IP address for their traffic, so some hosts experience an outage.
- ACL: You can always add a check for ACLs that cause a problem. Perhaps NAT has been configured correctly, but an ACL exists on one of the interfaces, discarding the packets. Note that the order of operations inside the router matters in this case. For packets entering an interface, IOS processes ACLs before NAT. For packets exiting an interface, IOS processes any outbound ACL after translating the addresses with NAT.
- User traffic required: NAT reacts to user traffic. If you configure NAT in a lab, NAT does not act to create translations (show ip nat translations) until some user traffic enters the NAT router on an inside interface, triggering NAT to do a translation. The NAT configuration can be perfect, but if no inbound traffic occurs that matches the NAT configuration, NAT does nothing.
- IPv4 routing: IPv4 routing could prevent packets from arriving on either side of the NAT router. Note that the routing must work for the destination IP addresses used in the packets.